Configure user store-based adaptive authentication¶
This page guides you through configuring user store-based adaptive authentication for a sample web application.
This is useful if you want to add security for users logging in from other user store domains.
Using the user store-based adaptive authentication template, you can allow certain user store domains so that users from the allowed domains are prompted to perform an additional level of authentication, while users from any other user store domain can simply provide their credentials (basic authentication) to access a resource.
Scenario¶
Consider a scenario where you want to step up authentication for users who belong to EMPLOYEES and CONTRACTORS user store domains. For users assigned to these user store domains, the login flow in applications should be stepped up with TOTP as follows:
- Basic authentication (username and password)
- TOTP or FIDO
Prerequisites¶
- See the general prerequisites for all adaptive authenticaiton scenarios.
- You need to set up the sample application.
- You need to set up a database. For this scenario, we will use an LDAP server.
-
You need to configure a new user store:
- On the management console, go to Main > Identity > User Stores > Add.
-
Create a user store named
EMPLOYEESand add the following values for the fields.Field name Value Connection URL ldap://localhost:10390 Connection Name uid=admin,ou=system Connection Password secret User Search Base ou=users,ou=system Username Attribute uid User Search Filter (&(objectClass=person)(uid=?)) User List Filter (objectClass=person) User ID Attribute uid User ID Search Filter (&(objectClass=person)(uid=?)) -
Expand the Optional tab and add the following:
Field name Value Group Search Base ou=groups,ou=system -
Click Update to save the configurations.
-
You need to add two users with login permissions, and add their Domain as specified:
- Username:
Alex; Domain:PRIMARY - Username:
Kim; Domain:EMPLOYEES
- Username:
Configure user store-based authentication¶
To configure user store-based authentication:
-
On the management console, go to Main > Identity > Service Providers > List.
-
Click Edit on the
saml2-web-app-pickup-dispatch.comservice provider. -
Expand the Local and Outbound Authentication Configuration section and click Advanced Configuration.
-
You will be redirected to Advanced Configuration, expand Script Based Conditional Authentication.
-
In the Templates section, click on the
+corresponding to the Role-Based template.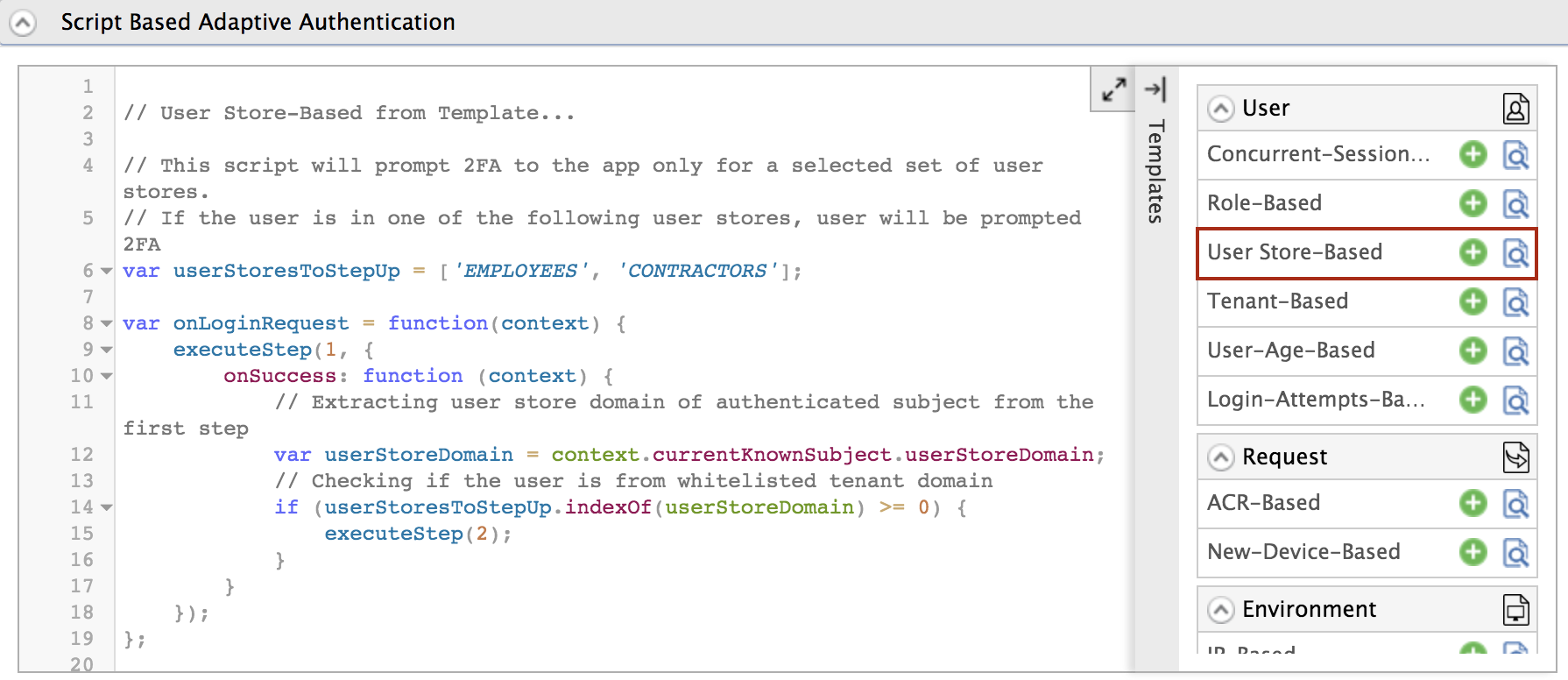
-
Click Ok to add the authentication script. The authentication script and authentication steps will be configured.
Info
- The authentication script prompts the second step of authentication for users that belong to the user stores named
EMPLOYEESandCONTRACTORS. - By default,
TOTPwill be added as the second authentication step. You can update this with any authentication method.
- The authentication script prompts the second step of authentication for users that belong to the user stores named
-
Click Update to save your configurations.
Create an LDAP Server¶
-
Open Apache Directory Studio.
-
On the LDAP Servers tab found on the bottom left corner,click New Server.
-
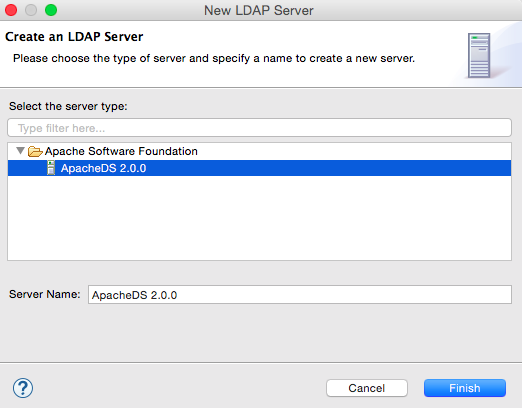
Select LDAP server ApacheDS 2.0.0 and click Finish.
-
Right-click on the newly created server and click Open Configuration.
-
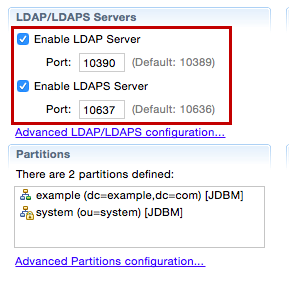
Port offset the LDAP and LDAP server ports by changing the LDAP port to 10390 and the LDAP server port to 10637. This ensures that the embedded LDAP server running in the prior installation of MWARE IAM does not conflict with the current installation.
-
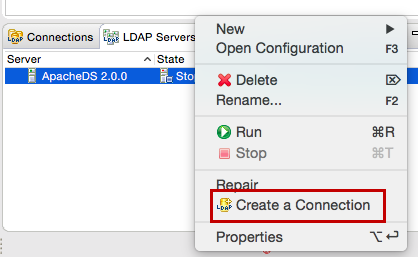
Right-click on the new server and click Create a Connection.
-
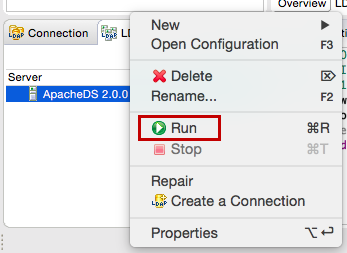
Right-click on the server and click Run to start the server.
Try it out¶
-
Access the following sample Pickup Dispatch application URL:
http://localhost.com:8080/saml2-web-app-pickup-dispatch.com -
Click Login and enter Alex's credentials.
Info
Note that Alex is successfully logged in to the application after going through only the basic authentication step.
-
Log out from the application and log in using Kim's credentials.
Info
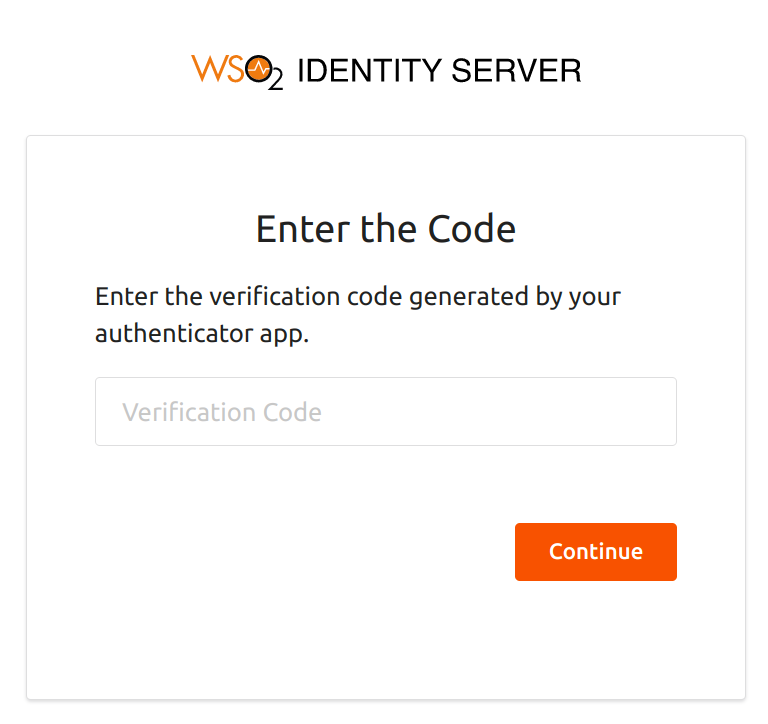
Note that Kim is prompted for the second step of authentication (i.e., TOTP) since she belongs to the user store domain
EMPLOYEES, which is within the list of user stores that should be stepped up. -
Enter the TOTP code and click Sign In.
Tip
Ensure that the LDAP server in Apache DS is running when attempting to log in as Kim.