Configure WS-Federation¶
To navigate to the federated authenticators configuration section, do the following.
-
Sign in. Enter your username and password to log on to the Management Console.
-
Navigate to the Main menu to access the Identity menu. Click Add under Identity Providers.
-
Fill in the details in the Basic Information section.
-
Expand the WS-Federation(Passive) Configuration form.
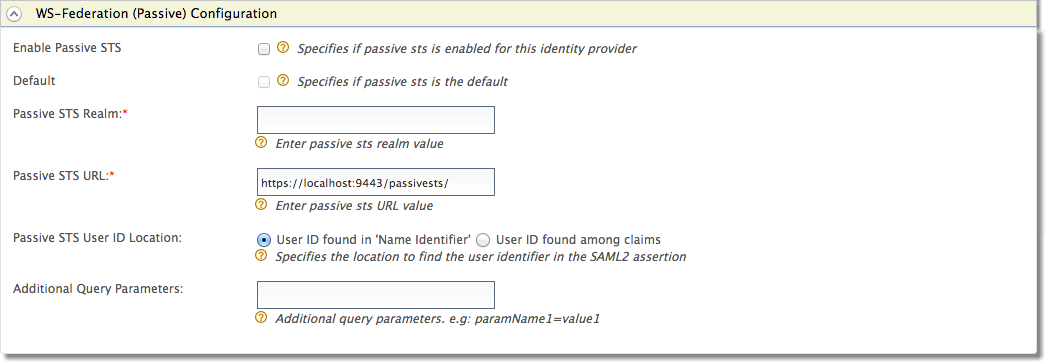
-
Fill in the following fields where relevant.
Field Description Sample value Enable Passive STS Selecting this option enables Passive STS to be used as an authenticator for users provisioned to the Identity Server. Selected Default Selecting the Default checkbox signifies that Passive STS is the main/default form of authentication. This removes the selection made for any other Default checkboxes for other authenticators. Selected Passive STS Realm This is used as an identifier for the realm and can be any value. WSFederationHealthCare Passive STS URL When sending the authentication request, there is a request for a security token generated by WS-Trust.
Note
As long as the federated IdP is the MWARE IAM, this URL must follow this format:https://(host-name):(port)/acshttps://localhost:9443/passivests/ Passive STS User ID Location Select whether the User ID is found in 'Name Identifier' as part of the authentication request or if it is found among the claims. This specifies how the user is identified. User ID found in 'Name Identifier' Additional Query Parameters This is necessary if you are connecting to another Identity Server or application. Sometimes extra parameters are required by this IS or application so these can be specified here. paramName1=value1
Configuring hostname verification
In previous releases, Passive STS Single-Logout (SLO) requests for
service providers were initiated without hostname verification which can
impose a security risk. From IS 5.2.0 release onwards, certificate
validation has been enforced and hostname verification is enabled by
default. If you want to disable the hostname verification, open the <IS_HOME>/repository/conf/deployment.toml file and add the following configuration.
[saml.slo]
host_name_verification: falseInfo
If the certificate is self-signed, import the service provider's public key to the IS client trust store to ensure that the SSL handshake in the SLO request is successful. For more information on how to do this, see Managing Keystores with the UI in the WSO2 Product Administration Guide.