Configuring Multi-factor Authentication with Username and Password¶
This scenario involves obtaining the username first and validating that before authenticating the user using the password.
Scenario¶
Consider a scenario where you want to log in users' to your application by validating the username and authenticating the user using the password that the user enters.
Prerequisites¶
- You need to set up the sample application.
Configure username validation¶
To configure MFA using username and password:
-
On the management console, go to Main > Identity > Service Providers > List.
-
Click Edit on the service provider you have created.
-
Expand the Local and Outbound Authentication Configuration section and click Advanced Configuration.
Info
see Configuring Local and Outbound Authentication for a Service Provider for more information.
-
Click Add Authentication Step twice to add two authentication steps for the application.
-
Select the following authenticators from the Local Authenticators dropdown.
Authentication step Local authenticator First step Identifier FirstSecond step Username & PasswordNote
The
Identifier Firstis not an authenticator, so having only the identifier in the authentication flow will fail the authentication. If there are no authenticators configured other than identifier, an error occurs when updating the service provider. -
Click Update to save your configurations.
Note
The reCAPTCHA validation capability is available for the Identifier First authentication flow handler as an update in MWARE IAM 6.1.0 from update level 32 onwards. See the instructions on how to upgrade the MWARE IAM.
Configure the server¶
By default, the username is not validated, and MWARE IAM does not check whether it exists in the user store.
To enable username validation for applications:
1. Add the following code segment to <IS_HOME>/repository/conf/deployment.toml file to start validating the username.
[authentication.authenticator.user_identifier]
name = "IdentifierExecutor"
enable = true
[authentication.authenticator.user_identifier.parameters]
validate_username = true- Restart the Identity Server.
Try it out¶
- Access the following sample PickUp application URL:
http://localhost.com:8080/saml2-web-app-pickup-dispatch.com - Click Login, and enter admin's username.
- On the next screen, enter admin's password and click Continue.
- You will be successfully logged in to the application. Logout of the application.
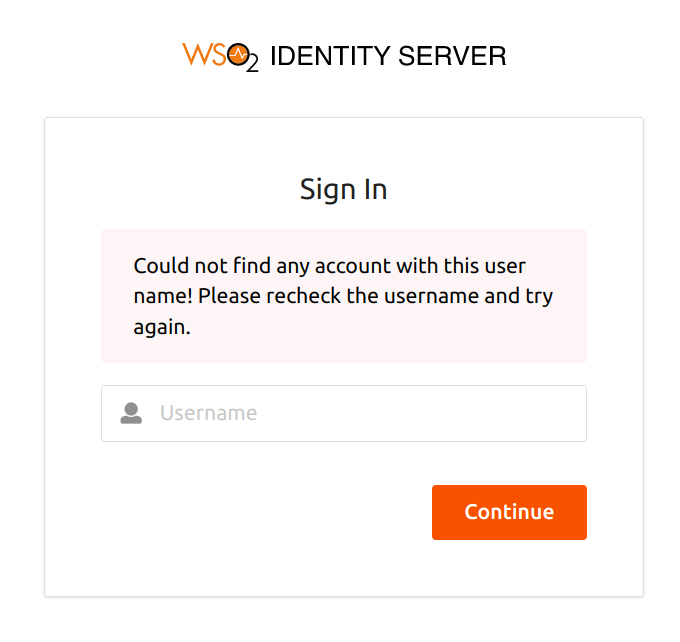
- Click Login again, and enter a username that is not registered on the IS.
-
Click Continue.
You will get an error message a user with the username you entered is not registered on the IS.