Configure Single-Sign-On with MWARE IAM via OpenID Connect¶
You can enable Single-sign-on for an ElasticSearch/Kibana deployment with MWARE IAM via OpenID Connect. To set this up, follow the steps given below.
Prerequisites¶
-
An Elasticsearch platinum subscription is required to enable SSO in ELK.
-
Configure ELK Analytics in MWARE IAM.
Configure a service provider at MWARE IAM¶
To enable SSO with MWARE IAM, a service provider needs to be created. Follow the steps given below to create a service provider.
-
Login to the MWARE IAM management console via https://{IS_HOST}:{PORT}/carbon
-
In the Main tab, click Add under Service Providers.

-
Provide a name for the service provider (eg. kibana) and click Regsiter.
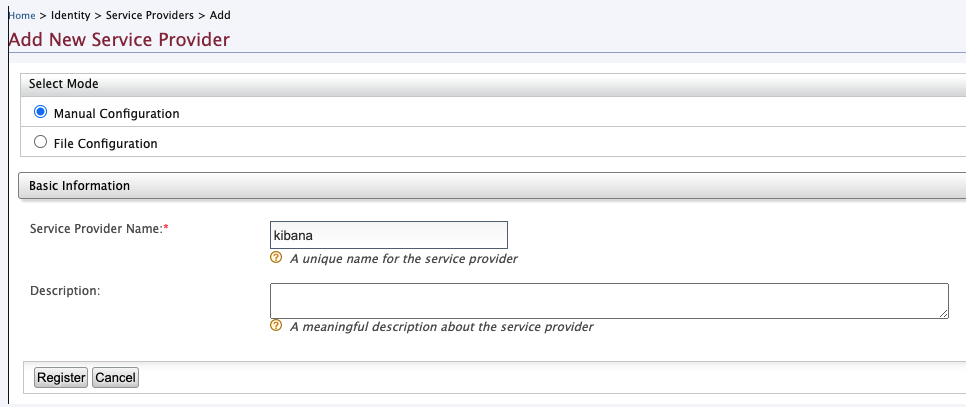
-
Once the service provider is created, expand its Claim Configuration section. Configure the claims as shown in the image below and click Update.

-
Expand the Inbound Authentication Configuration and under OAuth/OpenID Connect Configuration select Configure. Enter the following as the Callback Url.
regexp=(https://localhost:5601/api/security/oidc/callback|https://localhost:5601/security/logged_out)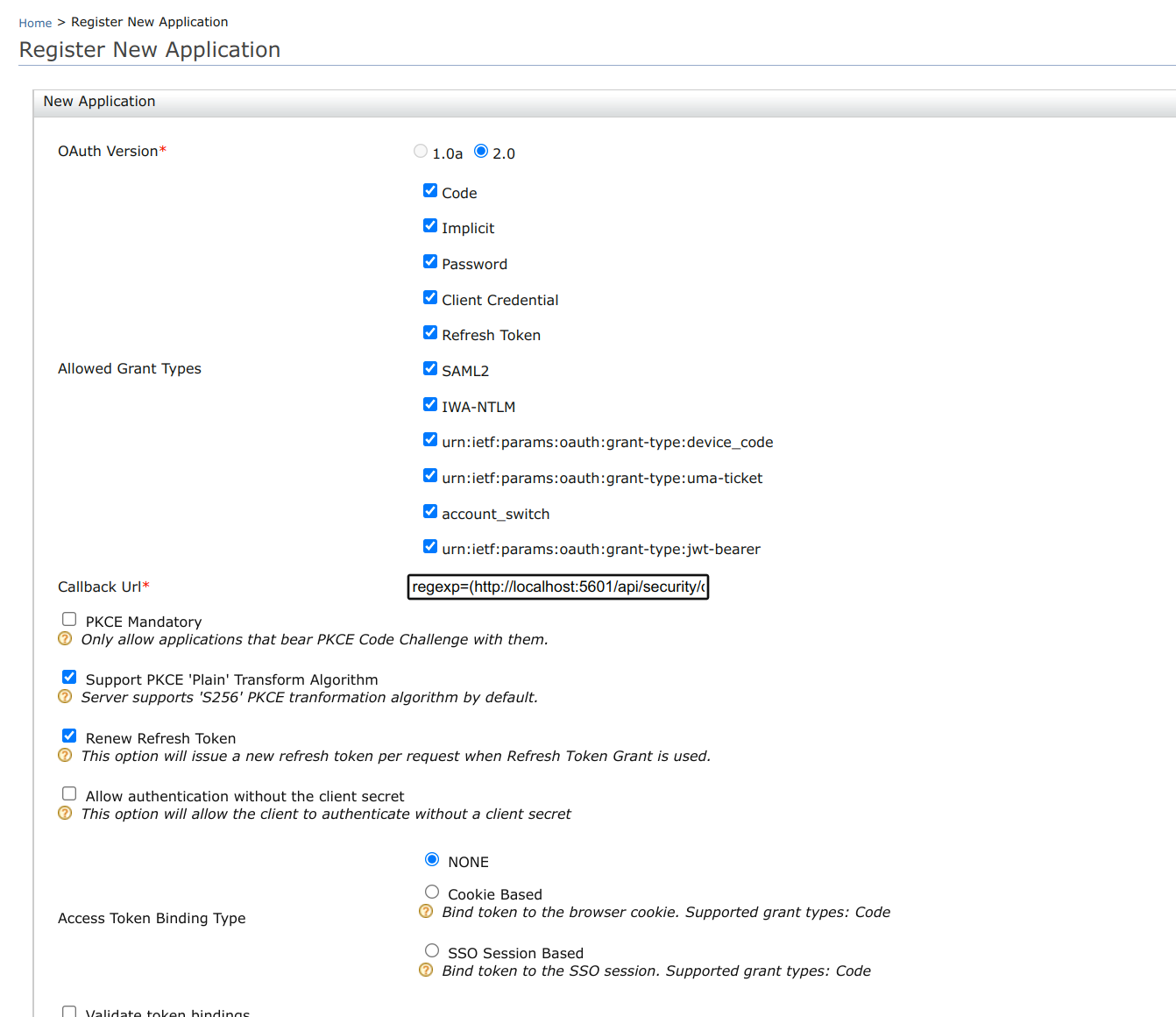
-
Click Update to save your changes.
-
Return to the Main tab of the MWARE IAM console and lick OIDC Scopes -> List under the Manage section.
-
Click Add claims in the Openid row. Add the claims you’ve used in step 4 and click Finish.
Configure OIDC Realm in Elasticsearch¶
To configure single sign-on in the Elastic Stack using OpenID connect, follow the steps given here.
A sample OpenID connect realm is as follows.
xpack.security.authc.token.enabled: true
xpack.security.authc.realms.oidc.oidc1:
order: 1
rp.client_id: "<<CLIENT ID>>"
rp.response_type: code
rp.redirect_uri: "http:///<KIBANA_HOST>:5601/api/security/oidc/callback"
op.issuer: "https://<IS_HOST>:<PORT>/oauth2/token"
op.authorization_endpoint: "https://<IS_HOST>:<PORT>/oauth2/authorize"
op.token_endpoint: "https://<IS_HOST>:<PORT>/oauth2/token"
op.jwkset_path: "https://<IS_HOST>:<PORT>/oauth2/jwks"
op.endsession_endpoint: "https://<IS_HOST>:<PORT>/oidc/logout"
op.userinfo_endpoint: "https://<IS_HOST>:<PORT>/oauth2/userinfo"
rp.post_logout_redirect_uri: "http://<KIBANA_HOST>:5601/security/logged_out"
claims.principal: sub
ssl.verification_mode: none
claims.groups: groups
claims.name: name
claims.mail: emailConfigure role mapping for Kibana Dashboard¶
Once the above steps are completed, role mapping needs to be configured in Kibana to allow MWARE IAM users to access the dashboards in Kibana. For that follow the steps below.
Create Users and Roles in MWARE IAM¶
- Login to the MWARE IAM management console via https://{IS_HOST}:{PORT}/carbon
-
From the Main menu in the left panel, click Add under the Users and Roles section.

-
In Add Users and Roles, click Add New Role

-
Create a role (eg.
AnalyticsViewer) and click Finish.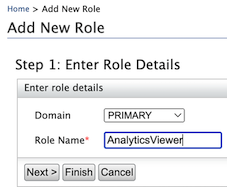
-
In Add Users and Roles, click Add New User.
-
Create a new user and click Next.

-
Assign the role that you created in step 4 to the user and click Finish.
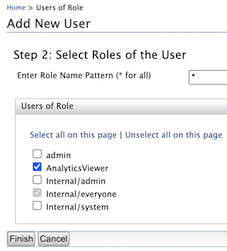
Configure role mapping in Kibana¶
-
Login to Kibana using basic authentication.
-
Click Stack Management on the left panel and then click Role Mappings under the Security section.
-
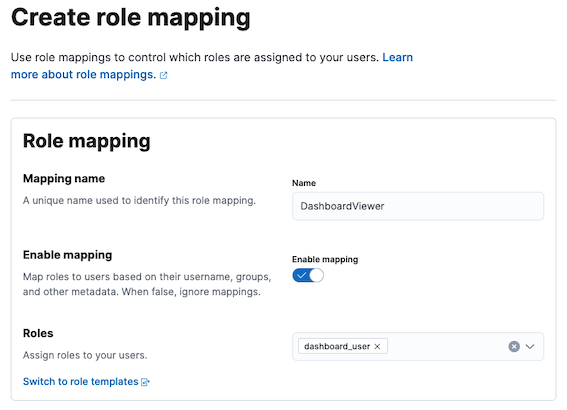
Click Create Role Mapping and add a new role mapping by giving a Mapping name.
-
Select a role that has access to the particular dashboard from Roles.
-
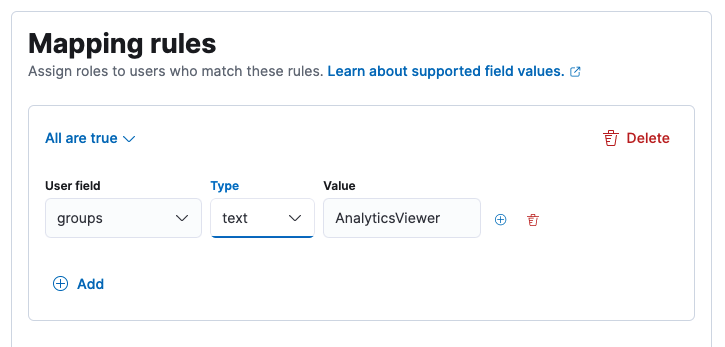
Click Add Rules under Mapping rules.
-
Select groups as the user field and enter the name of the role that you created in the MWARE IAM.
-
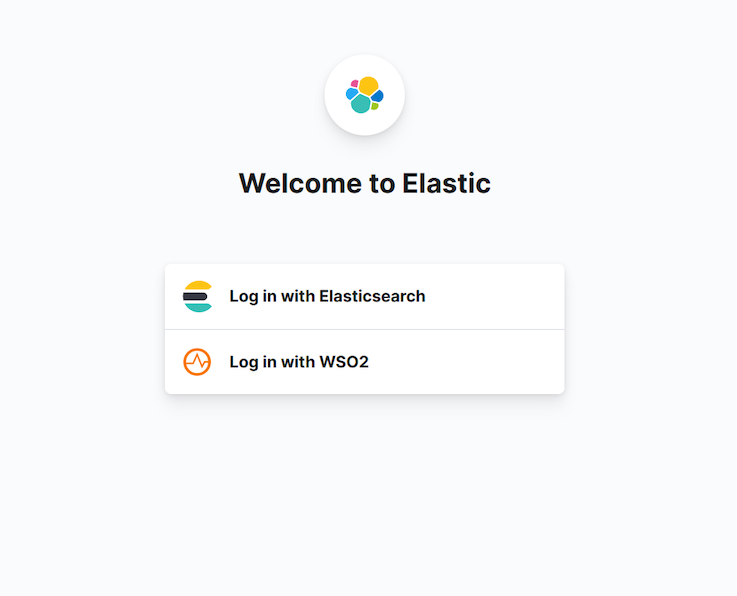
Logout from Kibana and re-login by selecting the Log in with WSO2 option.
-
This will navigate to the MWARE IAM login page. Try logging in with the credentials of the user that you created.
