Configure Kerberos Grant¶
This page guides you through the flow involved in exchanging a Kerberos ticket for an OAuth2 token. To learn more, see Kerberos grant.
Enable kerberos grant¶
-
Download the kerberos grant.jar file.
-
Copy the JAR into the
<IS_HOME>/repository/components/libdirectory. -
Add the following entry to the
<IS_HOME>/repository/conf/deployment.tomlfile.[oauth.grant_type.kerberos] enable = true
Create a service provider¶
To register your application as a service provider in the MWARE IAM:
-
Log in to the MWARE IAM Management Console using administrator credentials.
-
Go to Main > Identity > Service Providers > Add.
-
Enter a Service Provider Name. Optionally, enter a Description.
-
Click Register.
-
Expand Inbound Authentication Configuration and then OAuth/OpenID Connect Configuration.
-
Click Configure.
-
Select Kerberos from the Allowed Grant Types list.
-
Enter the Callback Url.
Tip
For more information on the
Callback Urlfield and other advanced configurations, see Advanced OpenID Connect Configurations. -
Click Add.
Note that the OAuth Client Key and Client Secret are generated. You will need these values later on when sending the request to the authorization endpoint.
-
Click Register.
Register an identity provider¶
-
Log in to the Management Console(
https://<IS_HOST>:<PORT>/carbon) using administrator credentials (admin:admin). -
On Main tab Click Identity > Identity Providers > Add.
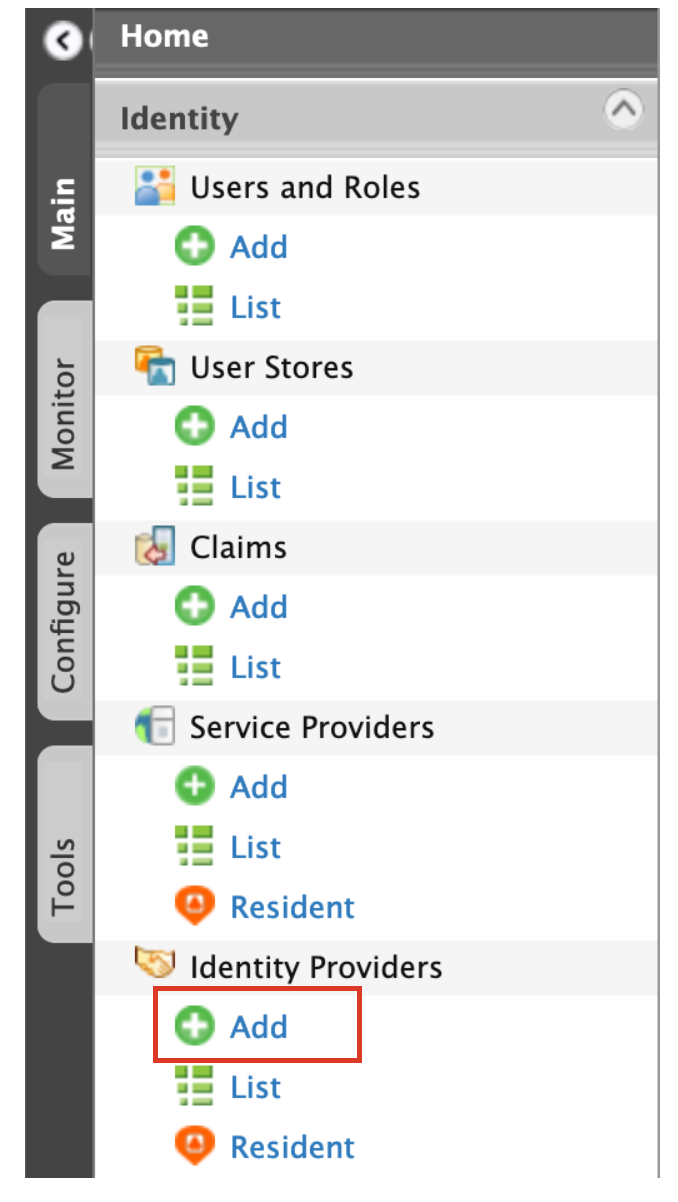
-
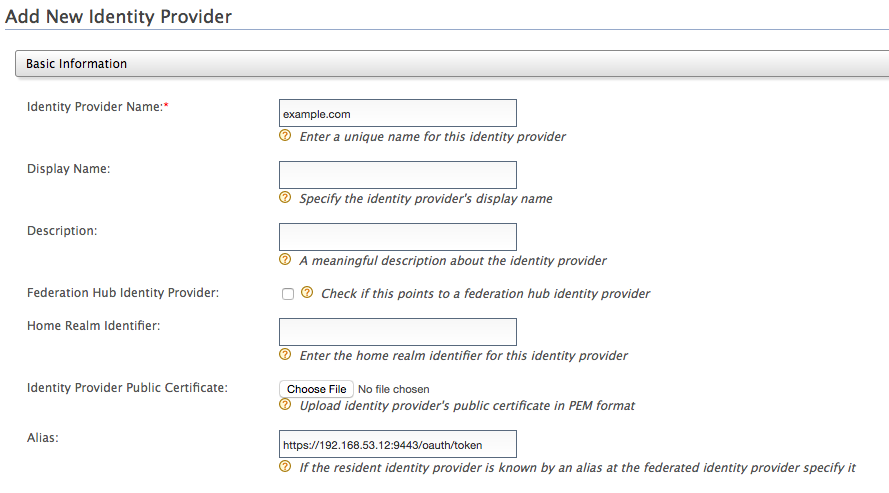
Add a new Identity Provider (IdP). Enter the basic information as follows.
Note
The IDP name should be the name of the realm as specified in step 3 of Generate the kerberos token. Based on this example, it should be
example.com.-
Identity Provider Name : example.com
-
-
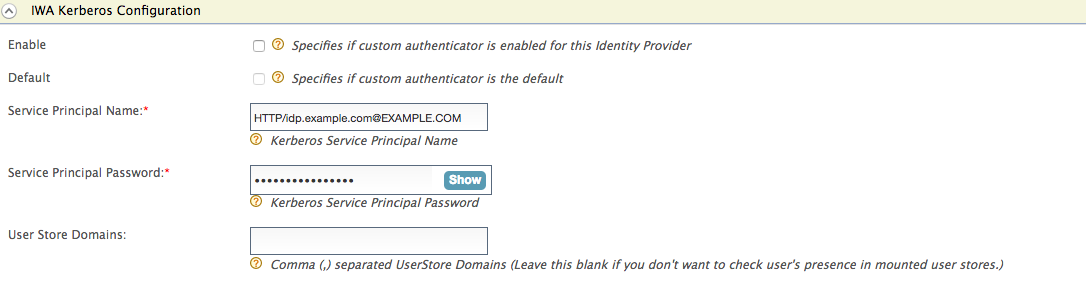
Expand the Federated Authenticators tab, and then the IWA Kerberos Configuration tab. Enter the required details as follows.
- Server Principal Name : HTTP/idp.example.com@EXAMPLE.COM
-
Server Principal Password: <password>
-
Click Register.
Generate the kerberos token¶
-
Git clone the KerbClientProject.
git clone https://github.com/erandacr/KerbClientProject -
Run
KerbClient.csusing an IDE.Tip
You can run it using Visual Studio by downloading and installing the following libraries and programs.
-
Visual Studio sdk(.NET Core 2.1)
-
Microsoft Visual Studio(Professional Edition)
-
Install
System.Net.Http.dlland define the path in theKerbClientProject.csprojfile.
Note that you can also use any other IDE to run this project.
-
-
Configure the following parameters in the project according to your setup.
// Service Name goes here static string serviceName = "HTTP/apimserver.example.com@EXAMPLE.COM"; // Token endpoint URL static string URI = "https://idp.example.com:9443/oauth2/token"; // Client ID static string username = "1ouL2fO6SxlfD2LDw125cTo0vQka"; // Client Secret static string password = "uUEtm89tY6QZuZUmqZfL92BDFeAa"; // Kerberos realm name static string realm_Name = "example.com"; -
Run the project by selecting the Start without Debugging option on the Visual Studio editor.
This project generates a Kerberos ticket and a kerberos token is generated using the ticket. The generated token can be used to get the OAuth token.
Invoke the token endpoint¶
Use one of the following curl commands to request for the OAuth token using the kerberos token.
Request 1
curl -v -X POST -H "Authorization: Basic <base64 encoded client id:client secret value>" -k -d "grant_type=kerberos&kerberos_realm=<kerberos realm>&kerberos_token=<kerberos token>" -H "Content-Type:application/x-www-form-urlencoded" https://localhost:9443/oauth2/tokenRequest 2
curl -u <client id>:<client secret> -k -d "grant_type=kerberos&kerberos_realm=<kerberos realm>&kerberos_token=<kerberos token>" -H "Content-Type:application/x-www-form-urlencoded" https://localhost:9443/oauth2/tokenYou will receive the following response.
POST /oauth2/token HTTP/1.1
Host: idp.example.com:9443
Content-Type: application/x-www-form-urlencoded
Authorization: Basic MW91TDJmTzZTeGxmRDJMRHcxMjVjVG8wdlFrYTp1VUV0bTg5dFk2UVp1WlVtcVpmTDkyQkRGZUFh
grant_type=kerberos&kerberos_realm=example.com&kerberos_token=YII1…The Kerberos client receives the OAuth2 token.
The Kerberos Grant then validates the received token with the provided Identity Provider (IdP) credentials and if it is a valid token, it issues an OAuth2 token to the client.
Example
{
"access_token":"636ce45f-c7f6-3a95-907f-d1f8aca28403",
"refresh_token":"831271d9-16ba-3bad-af18-b9f6592a8677",
"scope":"my_scope",
"token_type":"Bearer",
"expires_in":521
}Related topics