Introduction¶
You can configure the MWARE IAM to provision users to external applications.
See the Identity Server Architecture for more information on how this process fits into the overall picture.
Prerequisites¶
You need to register an identity provider on the Identity Server.
Configure outbound provisioning connectors¶
To configure outbound provisioning connectors:
- On MWARE IAM Management Console, go to Main > Identity > Identity Providers section.
- Click List, select the identity provider you want to enable Outbound provisioning on, and click on the corresponding Edit link.
-
Expand Outbound Provisioning Connectors, and select the connector that you would like to configure. Following are outbound provisioning connectors available.
Configure Google provisioning¶
To configure Google outbound provisioning:
- Expand Google Provisioning Configuration section.
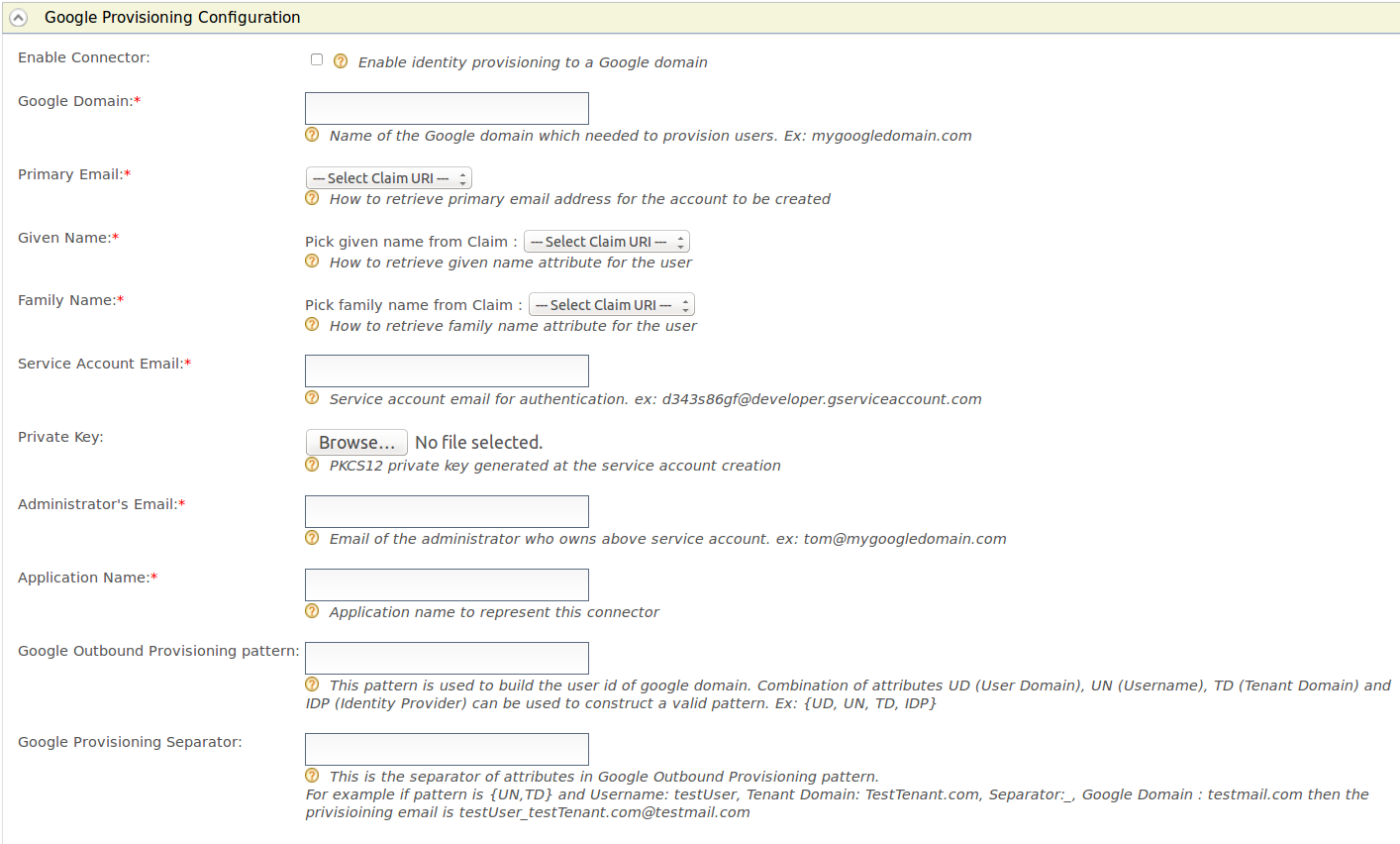
-
Fill in the following fields where relevant. The table contains all the configurations that can be done for Google outbound provisioning.
Field Description Sample Value Enable Connector Select this to enable identity provisioning through Salesforce. Selected Google Domain The name of the Google domain used to provision users. mygoogledomain.comPrimary Email Claim URI which will be used to retrieve the primary email address for the account to be created. This must be a claim that is available and local in the Identity Server. http://wso2.org/claims/emailaddressGiven Name The Claim URI used to retrieve the given name attribute for the user. This must be a claim that is available and local in the Identity Server. http://wso2.org/claims/givennameFamily Name Claim URI which will be used to retrieve the family name attribute for the user. This must be a claim that is available and local in the Identity Server. http://wso2.org/claims/lastnameService Account Email This email is used for authentication purposes. d343s86gf@developer.gserviceaccount.comPrivate Key Browse and attach the private key from your local machine. This is the PKCS12 private key generated at the service account creation Administrator's Email This is the email of the administrator who owns the service account in the Google Domain specified. Provisioning takes place using this email. om@mygoogledomain.comApplication Name This is the name of the application which is used to represent the Google connector. DomainGoogle Outbound Provisioning pattern This pattern is used to build the user ID of the Google domain. A combination of attributes UD (User Domain), UN (Username), TD (Tenant Domain), and IDP (Identity Provider) can be used to construct a valid pattern. {UD, UN, TD, IDP}Google Provisioning Separator This is used to separate the values you configure in the Google Outbound Provisioning pattern. _ -
Select Enable Connector to enable identity provisioning from Goolgle.
-
Click Update to dave the configurations.
Google Outbound Provisioning pattern
By using Google Outbound Provisioning pattern you differentiate the following scenarios:
- If there are several tenants and you must configure Google outbound provisioning for the same Google domain in those tenants.
- If there are several user stores and you must configure the specific user store that needs to be provisioned.
- If there are multiple identity providers configured for the same Google domain.
Configure Salesforce provisioning¶
This configuration involves setting up the Identity Server to send provisioning requests to Salesforce.
- Expand the Salesforce Provisioning Configuration form.
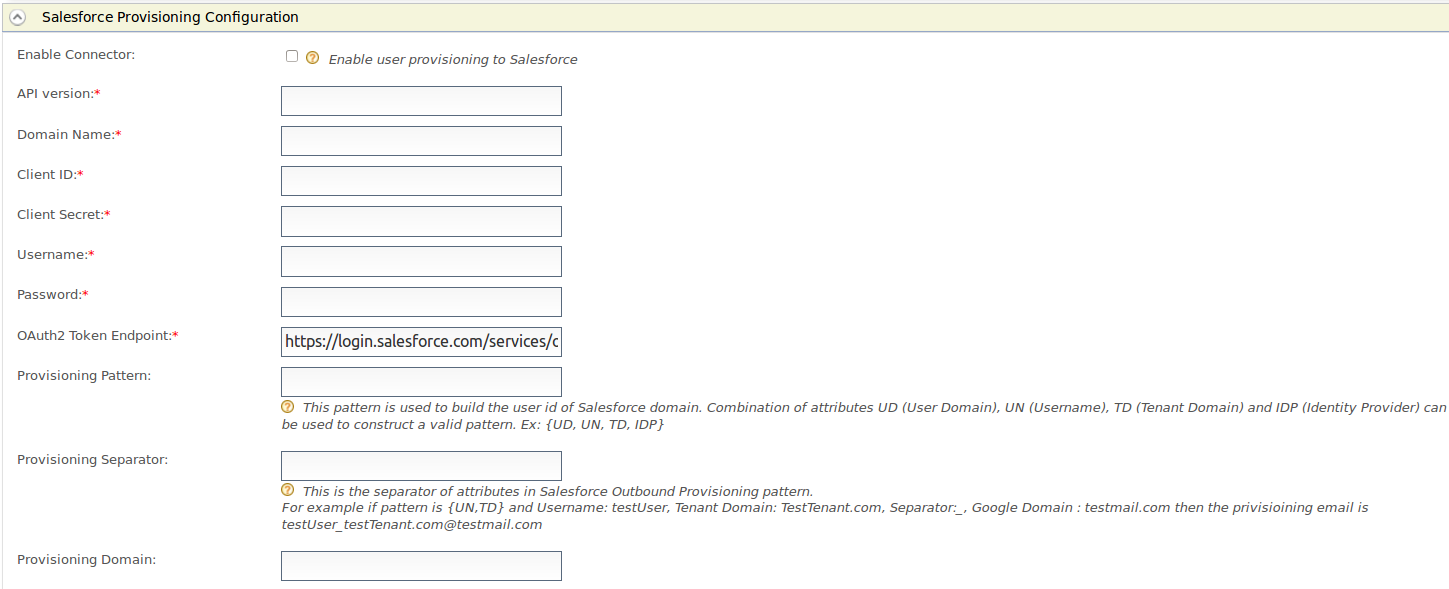
-
Fill in the following fields where relevant. The table contains all the configurations that can be done for Salesforce outbound provisioning.
Field Description Sample Value Enable Connector Select this to enable identity provisioning through Salesforce. Selected API version This is the version of the Salesforce API that is used for provisioning. v32.0Domain Name The name of the Salesforce domain used to provision users. https://identityprovisioning-dev-ed.my.salesforce.com/Client ID This is the username of the client you are using to access Salesforce. This Consumer Key value is obtained when configuring Salesforce. 3MVG8123wefw763na2452683KJNsvrgKBwe4gyksKJ22f3g45Client Secret This is the password of the client you are using to access Salesforce. This Consumer Secret value is obtained when configuring Salesforce. <password>Username This is the Salesforce username. samuel@wso2.comPassword This is the Salesforce password and must be entered along with the security token. OAuth2 Token Endpoint OAuth token endpoint URL of Salesforce. https://login.salesforce.com/services/oauth2/tokenProvisioning Pattern This pattern is used to build the user id of the Salesforce domain. A combination of attributes UD (User Domain), UN (Username), TD (Tenant Domain), and IDP (Identity Provider) can be used to construct a valid pattern. {UD, UN, TD, IDP}Provisioning Separator This is used to separate the values you configure in the Salesforce Outbound Provisioning pattern. _Provisioning Domain The user name of Salesforce is an email address. Here you can configure a specific domain name the username should have. yahoo.com -
Select Enable Connector to enable identity provisioning from Salesforce.
-
Click Update to dave the configurations.
Salesforce Outbound Provisioning pattern
By using Sales Outbound Provisioning pattern you differentiate the following scenarios:
- If there are several tenants and you must configure Salesforce outbound provisioning for the same Salesforce domain in those tenants.
- If there are several user stores and you must configure the specific user store that needs to be provisioned.
- If there are multiple identity providers configured for the same Salesforce domain.
Obtain Salesforce version
To obtain this:
- Log into https://developer.salesforce.com/.
- Click Setup .
- On the left navigation pane, click API under Develop.
- Generate one of the APIs to check the version.
Create a salesforce domain
To create a salesforce domain:
- Log in to https://developer.salesforce.com/.
- Click Setup.
- On the left navigation pane, click My Domain under Domain Management.
- Enter a Domain. Make sure you enter the domain with an HTTPS prefix to resemble a URL.
Claim configuration for Salesforce
The following claims must be configured when configuring Salesforce for outbound provisioning.
- EmailEncodingKey
- LanguageLocaleKey
- LastName
- LocaleSidKey
- ProfileId
- TimeZoneSidKey
- Username
- UserPermissionsCallCenterAutoLogin
- UserPermissionsMarketingUser
- UserPermissionsOfflineUser
See outbound provisioning with Salesforce for more information on how this is configured from end to end.
Configure SCIM provisioning¶
This configuration involves setting up the Identity Server to send provisioning requests to an external application that supports SCIM 1.1 or SCIM 2.0.
- Expand SCIM 1.1 Provisioning Configuration section or SCIM 2.0 Provisioning Configuration section as required.
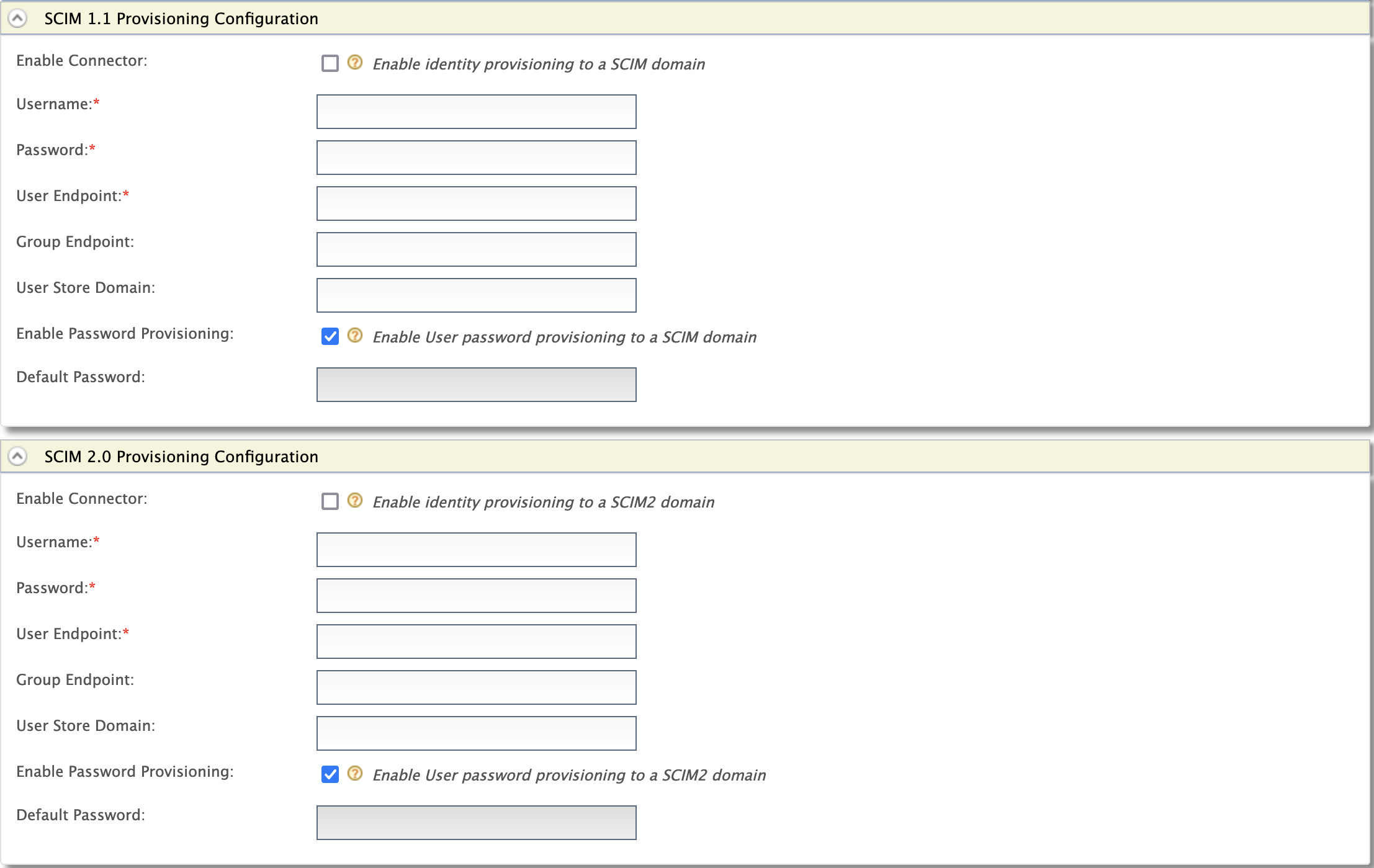
-
Enter the required fields. The table contains all the configurations that can be done for both SCIM 1.1 and SCIM 2.0 outbound provisioning.
Field Description Sample value Enable Connector Selecting this enables identity provisioning through SCIM. Selected Username This is the username of the SCIM application. AdminPassword This is the password of the SCIM application. \<password\>User Endpoint This is the SCIM endpoint of the users. For SCIM 1.1: https://localhost:9443/wso2/scim/UsersFor SCIM 2.0:https://localhost:9443/scim2/UsersGroup Endpoint This is the SCIM endpoint of the groups. For SCIM 1.1: https://localhost:9443/wso2/scim/GroupsFor SCIM 2.0:https://localhost:9443/scim2/GroupsUser Store Domain This is the user store that users are created. You can specify any user store connected to your identity provider. Domain Enable Password Provisioning This is to specify whether to send a default password or the password sent in the SCIM request, to the server where it gets provisioned. In a scenario where the Identity Server is used as a proxy, and sending the password to some other server is not appropriate, the default password can be sent. Selected Default Password The default password that must be sent. \<password\> -
Select Enable Connector to enable identity provisioning from SCIM.
- Click Update to dave the configurations.
See outbound provisioning with SCIM for more information on how this works in a typical scenario.
Custom Connectors
In addition to this, you can also create custom connectors that are added to the list of outbound provisioning connectors once created.