Log in to Google using the Identity Server¶
This page guides you through using MWARE IAM to log in to Google.
Before you begin!
You need to have a Google domain. Click here for more information on creating the domain.
Configure Google¶
-
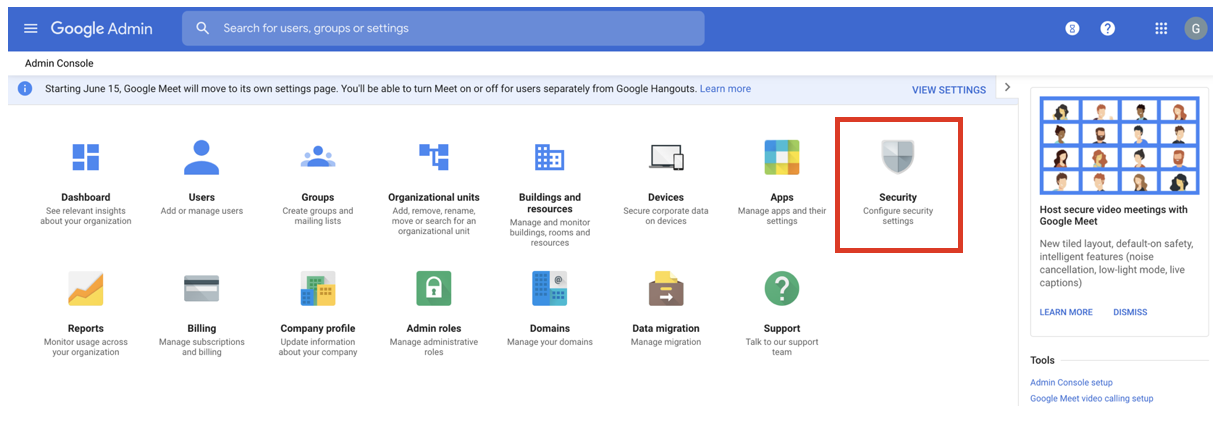
Access your domain's admin console via https://admin.google.com.
-
Click Security.
Info
Can't see the Security section? Click the MORE CONTROLS bar at the bottom and you can see the Security section.
-
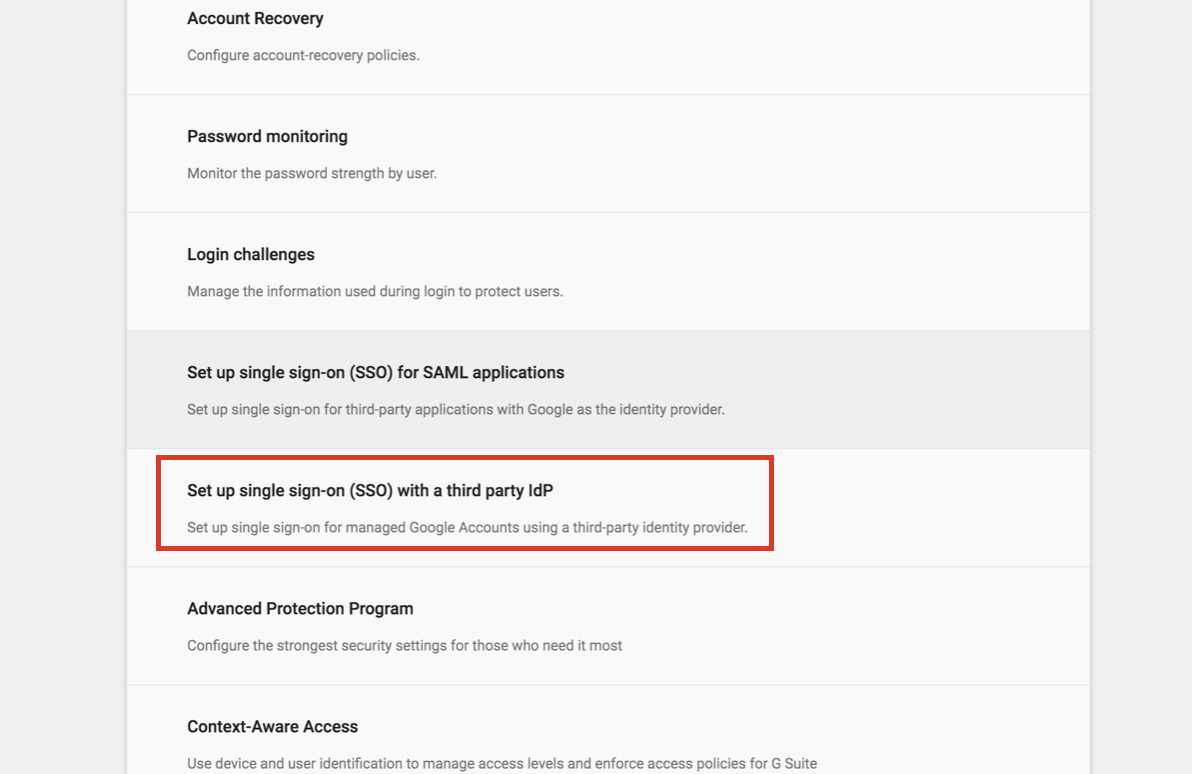
Click Set up single sign-on (SSO) with a third party IdP.
-
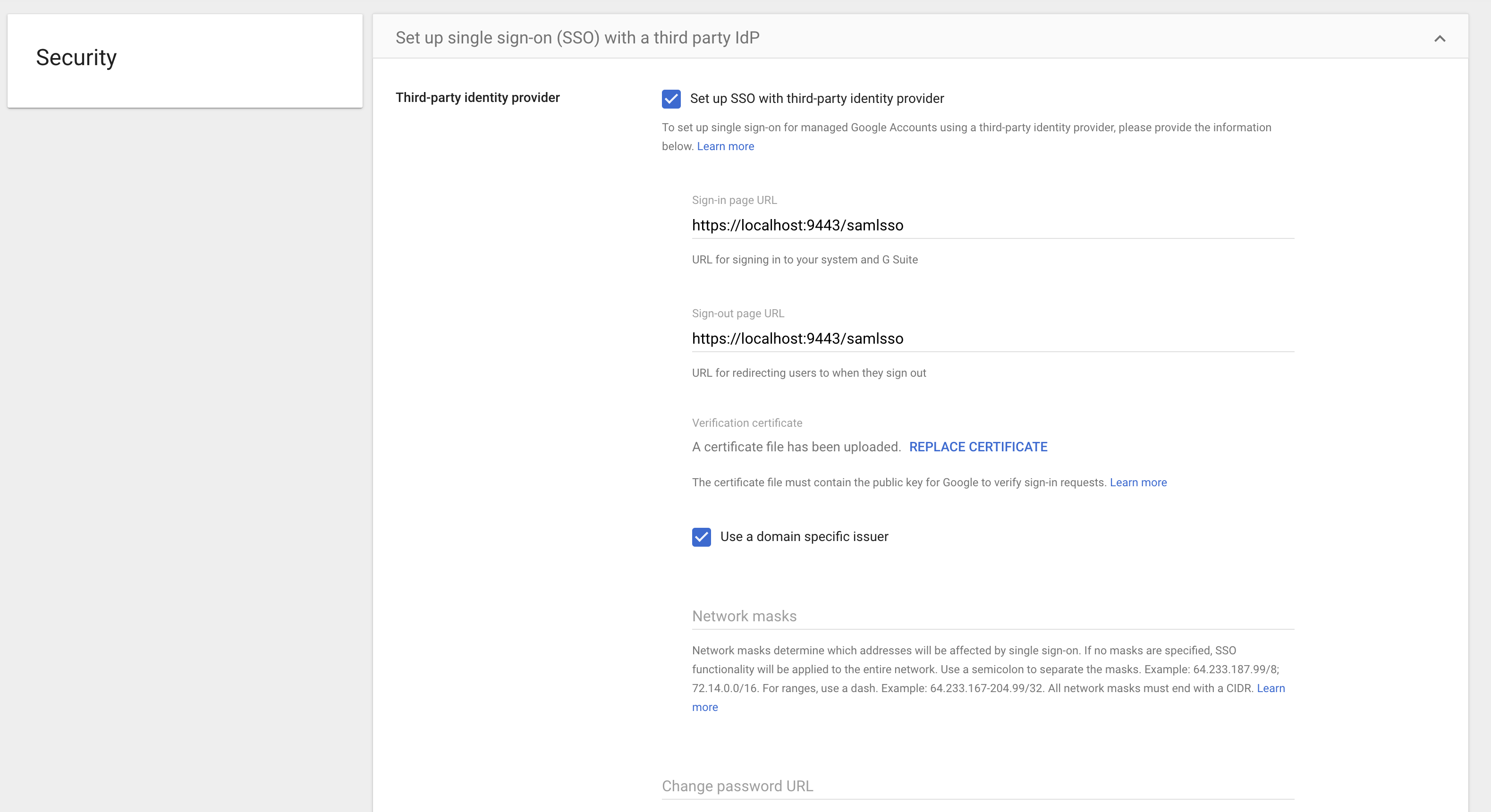
Enter the following URLs to your third-party Identity Provider (IdP).
-
Sign-in page URL:
https://<IS_HOSTNAME>:<IS_PORT>/samlsso -
Sign-out page URL:
https://<IS_HOSTNAME>:<IS_POST>/samlsso
-
-
Upload the Identity Server certificate:
The certificate file must contain the public key for Google to verify the sign-in requests.- Navigate to the
<IS_HOME>/repository/resources/securitydirectory via the terminal. -
Run the command given below to import the public certificate from the keystore to a
.pemfile.keytool -export -alias wso2carbon -keystore wso2carbon.jks -storepass wso2carbon -file mycert.pemInfo
The
mycert.pemfile is created in the same directory mentioned in step a above. If you want to change the name of the file that is being generated, enter a preferred name instead ofmycertin the above command. -
Click Replace certificate and upload the
.pemfile you just generated. -
Click Save.
- Navigate to the
Configure Email Address as the Username¶
Warning
Configuring the email address as the username in an already running Identity Server is not the production recommended way. Therefore, make sure to configure it before you begin working with MWARE IAM.
-
Log in to the Management Console and click Claims > List > http://wso2.org/claims.
-
Click the Edit link corresponding to the Username claim and configure the
Mapped Attributeproperty tomail.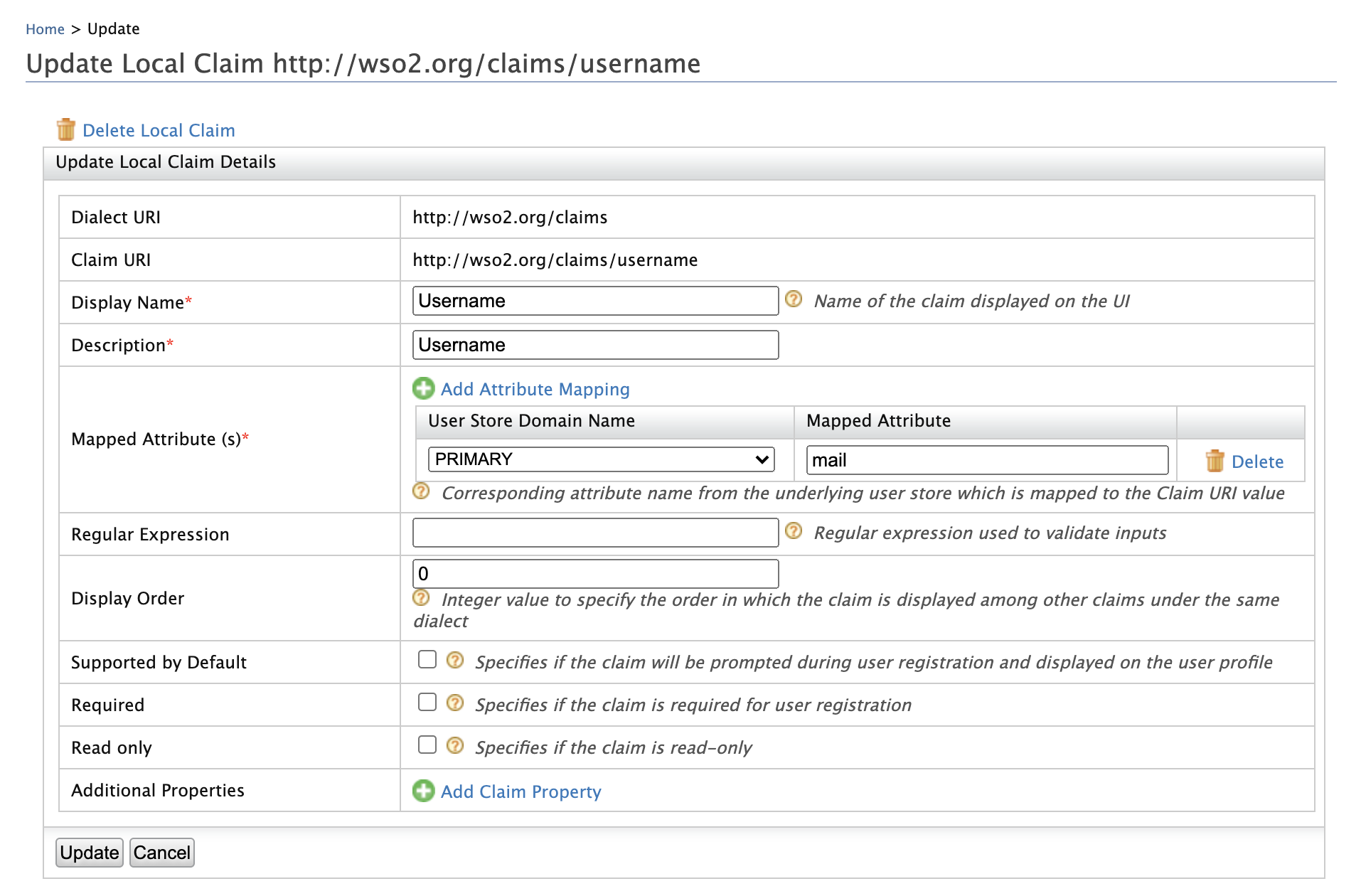
-
Click Update to save the changes.
-
Open the
<IS_HOME>/repository/conf/deployment.tomlfile. -
Add the following configuration to enable email authentication.
[tenant_mgt] enable_email_domain= true -
Configure the following set of parameters in the userstore configuration, depending on the type of userstore you are connected to (LDAP/Active Directory/ JDBC).
Parameter Description UserNameAttribute
Set the mail attribute of the user. LDAP/Active Directory only
[user_store]
user_name_attribute = "mail"UserNameSearchFilterUse the mail attribute of the user instead of
cnoruid. LDAP/Active Directory only
For example:In LDAP,
[user_store]
user_name_search_filter ="(&(objectClass=person)(mail=?))"
In Active Directory,[user_store]
user_name_search_filter ="(&(objectClass=user)(mail=?))"UserNameListFilterUse the mail attribute of the user if necessary. LDAP/Active Directory only
For example:In LDAP,
[user_store]
user_name_list_filter ="(&(objectClass=person)(!(sn=Service)))"
In Active Directory,[user_store]
user_name_list_filter ="(&(objectClass=user)(!(sn=Service)))"UsernameJavaScriptRegExChange this property that is under the relevant userstore manager tag as follows. This property allows you to add special characters like "@" in the username.
[user_store]
username_java_script_regex = '^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,4}$'UsernameJavaRegExThis is a regular expression to validate usernames. By default, strings have a length of 5 to 30. Only non-empty characters are allowed. You can provide ranges of alphabets, numbers and also ranges of ASCII values in the RegEx properties.
[user_store]
username_java_regex = '^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,4}'Realm configurations The username must use the email attribute of the admin user.
[super_admin]
username = "admin@wso2.com"
password = "admin"Note
Before this configuration, the user having the username admin and password admin was considered the super administrator. The super administrator user cannot be deleted.
After this configuration, the user having the username
admin@wso2.comis considered the super administrator. The user having the username admin is considered as a normal administrator.
Info
- With these configuration users can log in to super tenant with both
email username (
alex@gmail.com) or non-email usernames (larry). However, for tenants, only email usernames are allowed. (tod@gmail.com@wso2.com). - You can configure email username without enabling the
enable_email_domainproperty (step 5). Then users can log in to both the super tenant and the tenant using email and non-email usernames. However, super tenant users should always use @carbon.super at the end of usernames.
- With these configuration users can log in to super tenant with both
email username (
-
Restart the server.
Create the service provider¶
To register your application as a service provider in the MWARE IAM:
-
Log in to the MWARE IAM Management Console using administrator credentials.
-
Go to Main > Identity > Service Providers > Add.
-
Enter a Service Provider Name. Optionally, enter a Description.
-
Click Register.
SAML Configurations¶
Make the following changes to the created service provider.
-
Expand Inbound Authentication Configuration > SAML Configuration and click Configure.
-
Fill in the value for Issuer and Assertion consumer URL as shown below.
Field Value Description Issuer google.comThis is the <saml:Issuer>element that contains the unique identifier of the service provider.Assertion Consumer URL https://www.google.com/a/<ENTER_YOUR_DOMAIN>/acsThis is the URL to which the browser should be redirected to after the authentication is successful. This is the Assertion Consumer Service (ACS) URL of the service provider. The identity provider redirects the SAML2 response to this ACS URL. However, if the SAML2 request is signed and SAML2 request contains the ACS URL, the Identity Server will honor the ACS URL of the SAML2 request. -
Select Enable Response Signing to sign the SAML2 Responses returned after the authentication process.
-
Select Enable Attribute Profile and Include Attributes in the Response Always so that the the identity provider will always include the attribute values related to the selected claims in the SAML2 attribute statement.
-
Click Register.
Try it out¶
Now, you have successfully configured Google and MWARE IAM.
Note
The admin users of your Google domain do not get redirected to MWARE IAM. Therefore, to try out the tutorial you need to use a user who is not an admin in your Google account.
-
Create a user in MWARE IAM. Make sure that the same user exists in your Google domain.
In this example,alex@wso2support.comis in the Google domain. Therefore, we need to create the same user in MWARE IAM.- Log in to the MWARE IAM Management Console (
https://<IS_HOST>:<PORT>/carbon) using administrator credentials (admin:admin).
- Log in to the MWARE IAM Management Console (
-
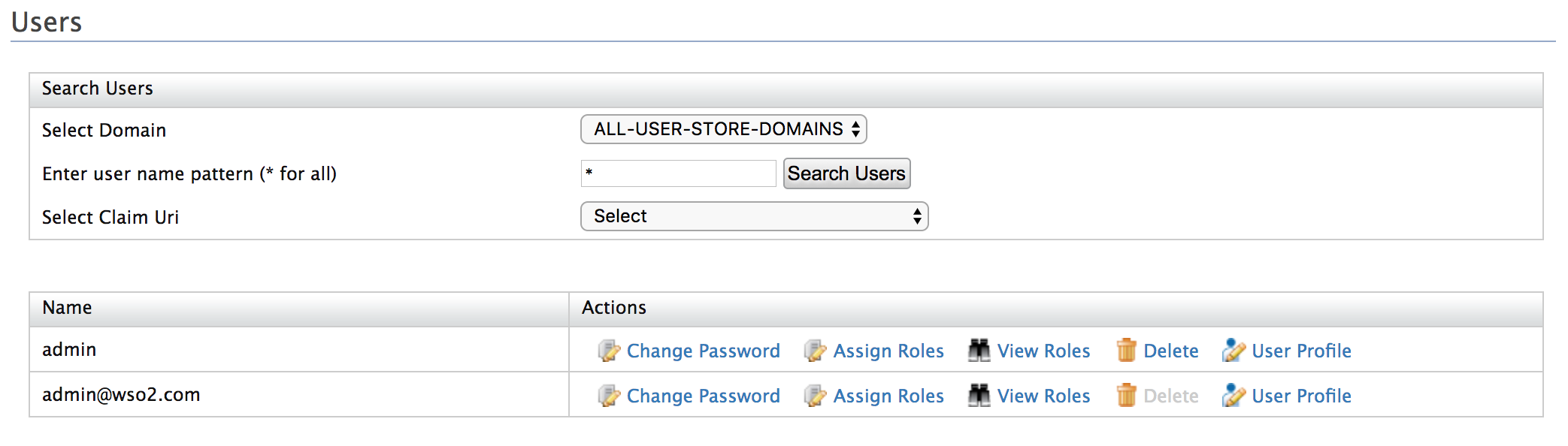
Navigate to Main > Identity > Users and Roles > Add.
-
Click Add New User and enter username and password. When adding a new user, use an email address as the username. Since it is not mandatory to assign a role to a user in this tutorial, click Finish.
-
Navigate to
https://google.com/a/<ENTER_YOUR_DOMAIN>/acsand enter the email address (username) of the user you created.
You are navigated to MWARE IAM's sign in screen. - Enter the username and password of the user you created.
You are navigated to the G-Suite of that domain and you can select the application you need to use.
Tip
If you want to only access Gmail, navigate to mail.google.com, enter the username of the user, enter the username and password of the user on the WSO2 Identity Server sign in screen, and you are navigated to the user's mail account.
Related topics