Configure Outbound Provisioning with Salesforce¶
The MWARE IAM has the ability to provision users into different domains like Salesforce, Google, Facebook, etc., using its identity provisioning framework.
This topic provides instructions on how to configure Salesforce as the Identity Provider to provision users from MWARE IAM. The service provider in this scenario is MWARE IAM. When MWARE IAM is the service provider, it is configured as the resident Service Provider. Therefore, after completing this tutorial you can see the users you add using MWARE IAM being created in Salesforce too.
Configure Salesforce¶
-
Sign up as a Salesforce developer.
- Fill out the relevant information found in the following URL: https://developer.salesforce.com/signup
- Click Sign me up.
- Click Allow to enable Salesforce to access your basic information. This message pops up only when you log in to Salesforce for the first time.
Note
This document is explained using the Salesforce lightning theme. If you are using the classic theme, click Switch to Lightning Experience on the top panel.
You will be navigated to the lightening theme of Salesforce.
-
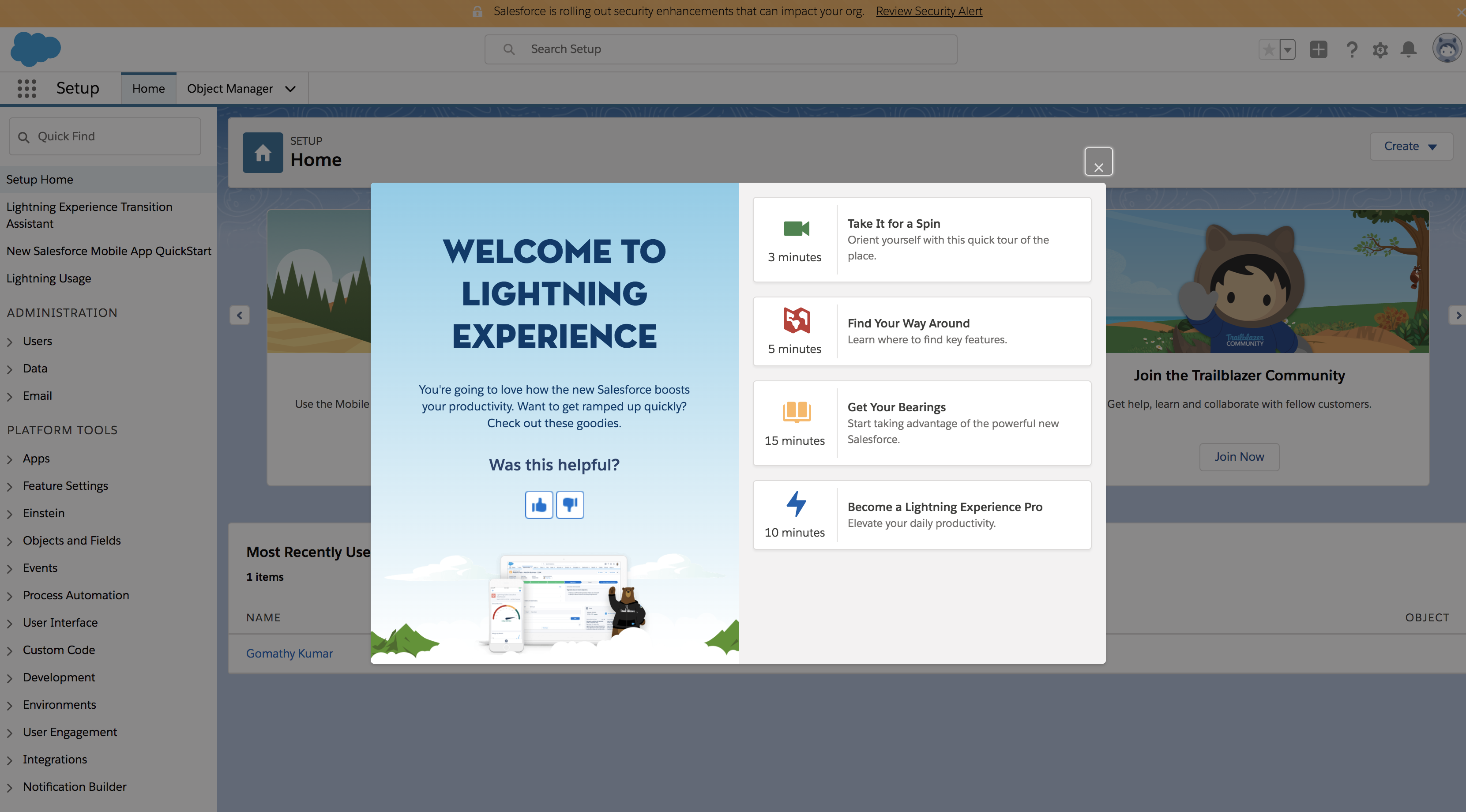
Once you are logged in, add a connected app. Follow instructions below on how to do this.
-
Expand the Apps options in the left panel and click on App Manager.
-
Click on New Connected App.
-
Fill in the form that appears with relevant details. The following table describes the form labels in detail.
Form Label Description Connected App Name The name of the connected app. For example, IdentityServerProvisioning. API Name Enter the API name used when referring to your app from a program. The API name should match the name of the connected app. This defaults to a version of the name without spaces. Only letters, numbers, and underscores are allowed, so you must edit the default name if the original app name contains any other characters. Contact Email The email address used by the connected app. Enable OAuth Settings This section controls how your app communicates with Salesforce. Select the checkbox to enable OAuth settings to configure authentication settings. Callback URL The Callback URL is used for redirection. This is typically the URL that a user’s browser is redirected to after successful authentication. Use the following value here: https://login.salesforce.com/services/oauth2/tokenSelected OAuth Scopes Choose Full access (full) from the Available OAuth Scopes and click the button under Add. This gives the necessary permissions when accessing this app.
These scopes refer to permissions the user gives to the connected app while it is running. The OAuth token name is in parentheses.
Full access (full) allows access to the logged-in user’s data, and encompasses all other scopes. Full does not return a refresh token. You must explicitly request the refresh_token scope to get one.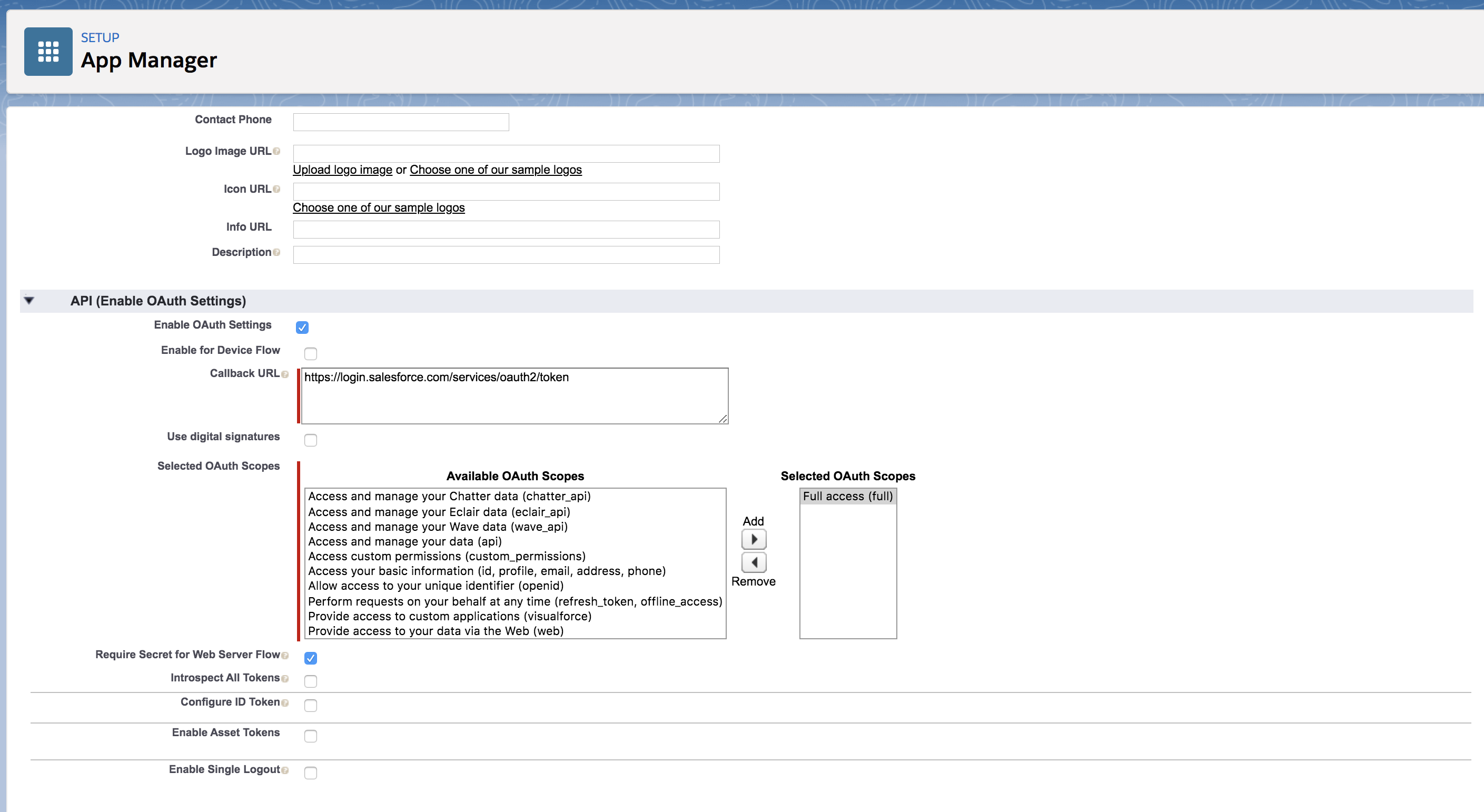
-
Click Save > Continue to add the connected app.
-
-
The resulting screen displays key information that you will need to configure MWARE IAM to Salesforce.
Make a note of the following details as you need them in upcoming configurations.- Consumer Key
- Consumer Secret (Click the Click to reveal link to view the consumer secret)
- Callback URL
Info
Consumer Key : A value used by the consumer to identify itself to Salesforce. Referred to as
client_idin OAuth 2.0. Consumer Secret : A secret used by the consumer to establish ownership of the consumer key. Referred to asclient_secretin OAuth 2.0.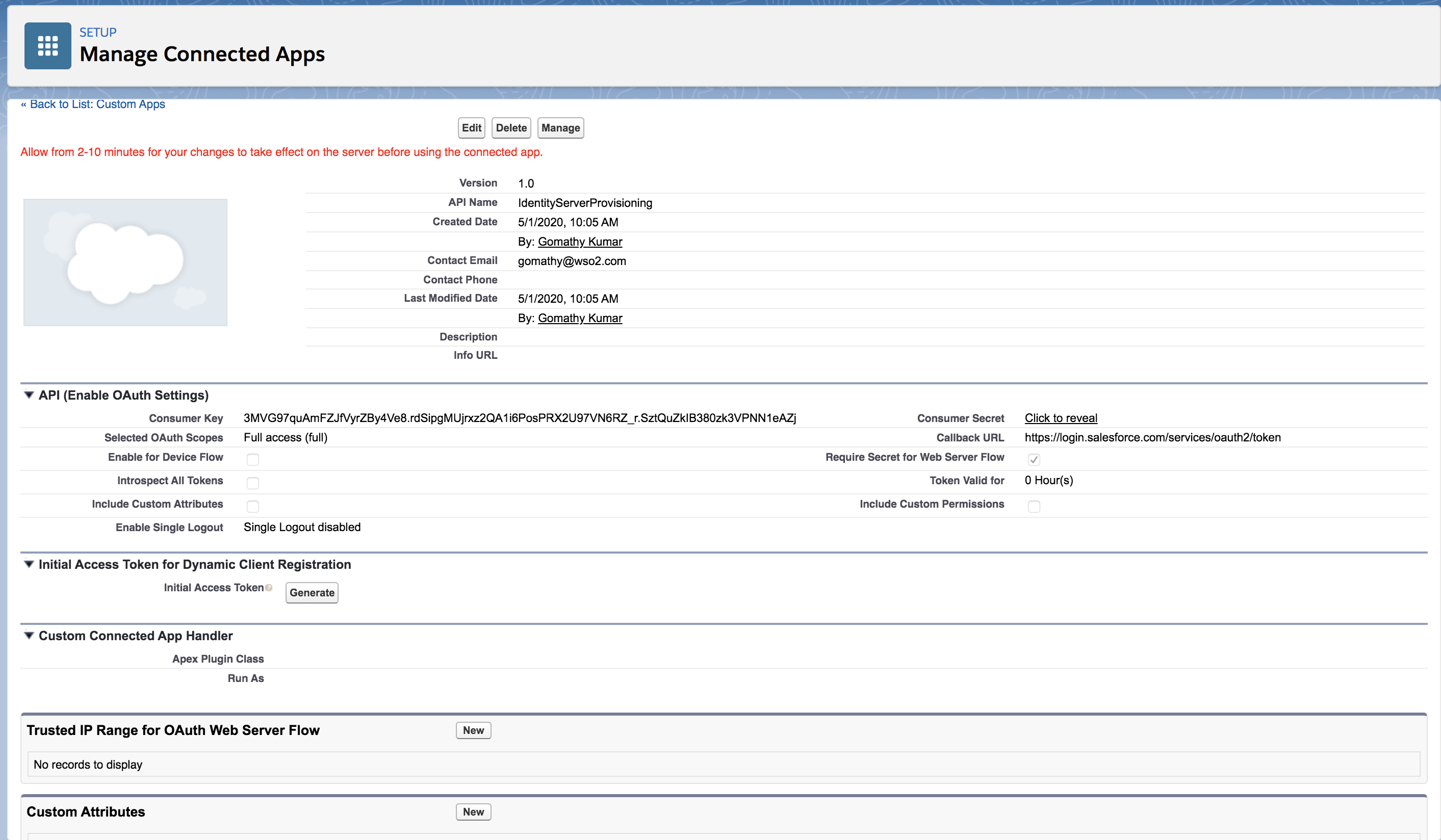
-
Add your connected app to the profile you are going to use. This is necessary as this profile is used when you add users in to Salesforce from the Identity Server.
Note
Allow from 2-10 minutes for your changes to take effect on the server before using the connected app.
-
Expand Users in the Administration section of the left hand panel and click Profiles. A list of existing profiles can be viewed.
-
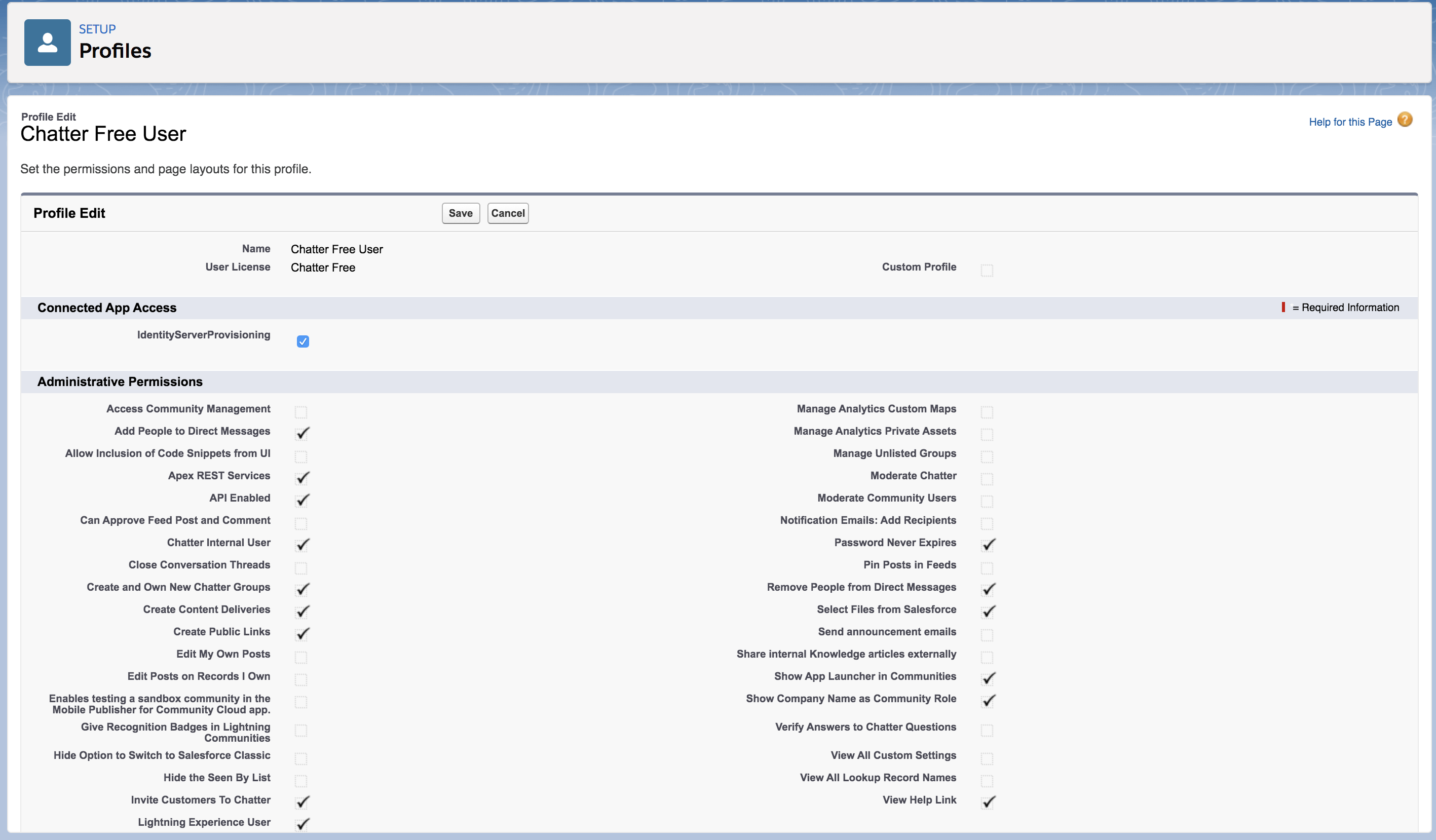
As an example, if you use the profile “Chatter Free User”, click Edit and select the connected app you created to configure with the Identity Server using the provided checkbox.
-
Click Save. Make a note of the profile ID (or address URL obtained from the address bar in your browser) of the Chatter Free User profile.
Tip
Copy the URL and decode it using a URL decoder like [urldecoder.org].
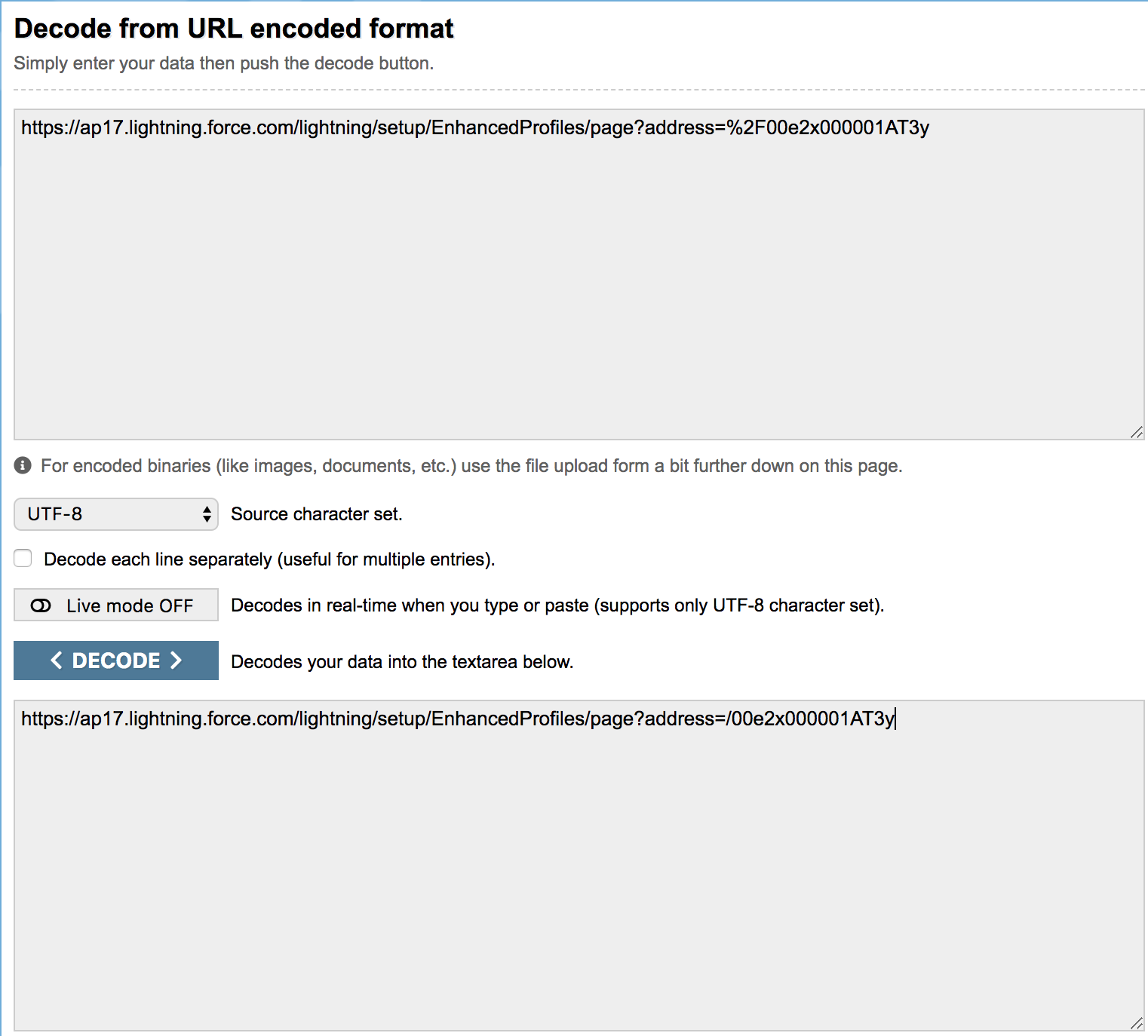
In this case
00e2x000001AT3yis your profile ID.
-
-
Get the public certificate for Salesforce. Do the following in order to achieve this.
Info
For more information on generating the certificate, see the Salesforce documentation.
-
In the left navigation panel, Expand Security and click Certificate and Key Management or you can search for Certificate and Key Management in the Quick Find search box.
-
Click Create Self-Signed Certificate.
- Enter the Label and a Unique Name and click Save.
The certificate is generated.
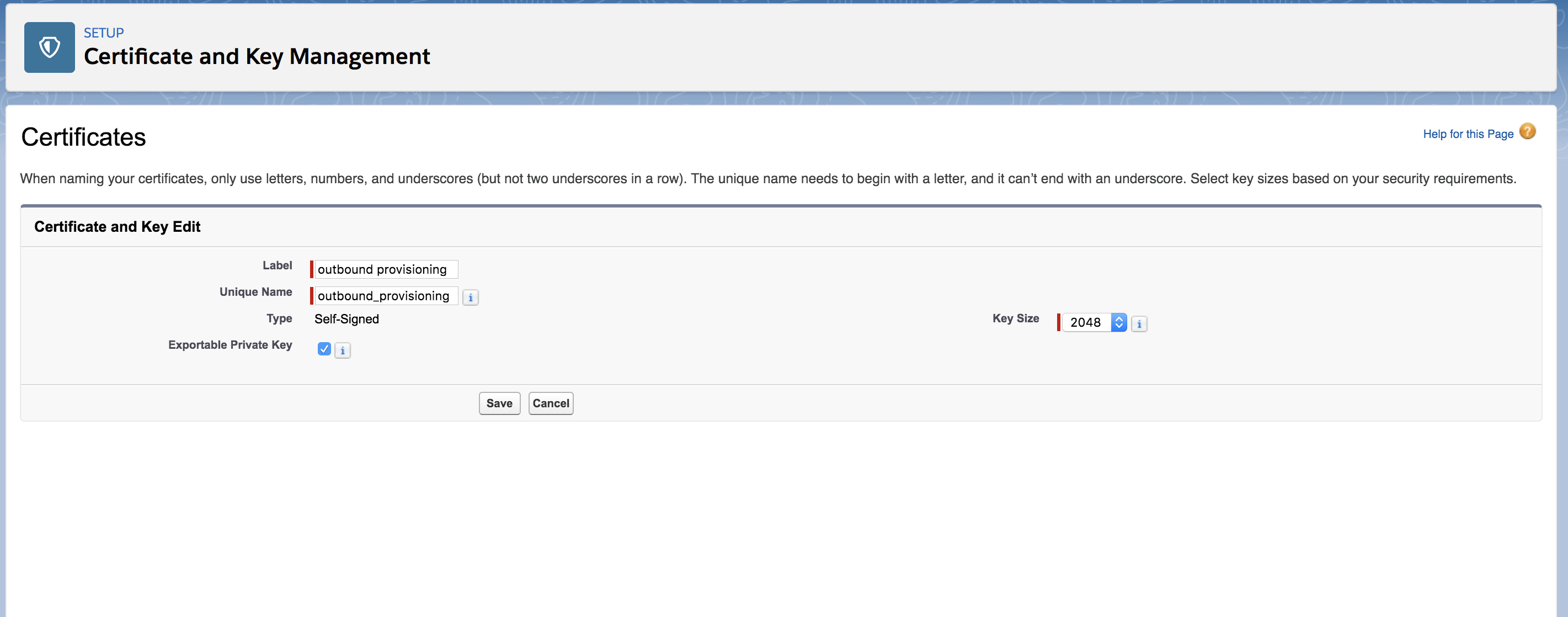
- Click the Download Certificate button to download the certificate.
-
Configure email address as the username¶
Provisioning is the process of coordinating the creation of user accounts, e-mail authorizations in the form of rules and roles, and other tasks such as provisioning of resources associated with enabling new users.
When you log into Salesforce, you normally use an email address. So, to integrate this with the Identity Server, you need to configure MWARE IAM to enable users to log in using their email addresses. In order to do that, follow the steps given below.
Warning
Configuring the email address as the username in an already running Identity Server is not the production recommended way. Therefore, make sure to configure it before you begin working with MWARE IAM.
-
Log in to the Management Console and click Claims > List > http://wso2.org/claims.
-
Click the Edit link corresponding to the Username claim and configure the
Mapped Attributeproperty tomail.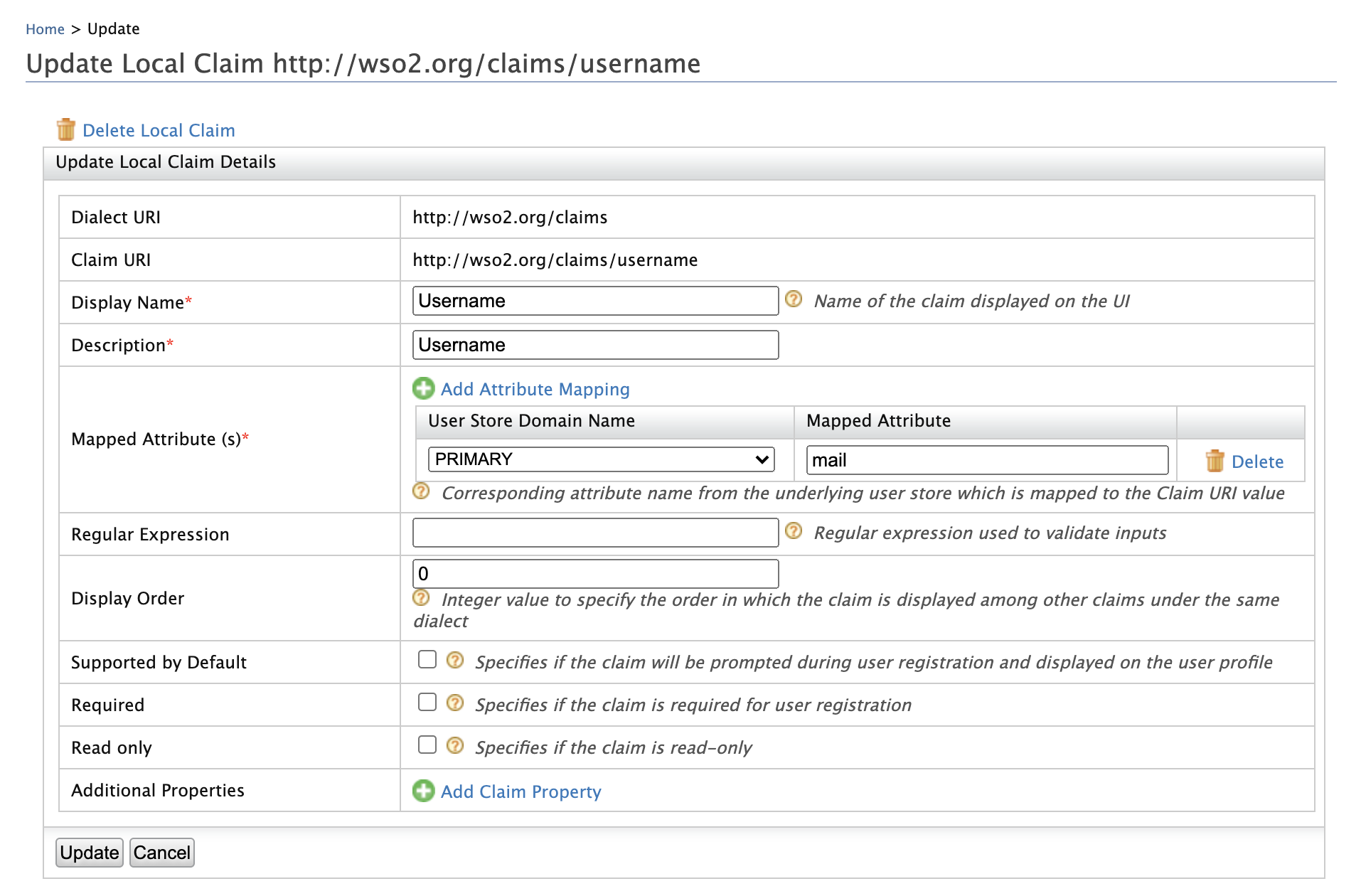
-
Click Update to save the changes.
-
Open the
<IS_HOME>/repository/conf/deployment.tomlfile. -
Add the following configuration to enable email authentication.
[tenant_mgt] enable_email_domain= true -
Configure the following set of parameters in the userstore configuration, depending on the type of userstore you are connected to (LDAP/Active Directory/ JDBC).
Parameter Description UserNameAttribute
Set the mail attribute of the user. LDAP/Active Directory only
[user_store]
user_name_attribute = "mail"UserNameSearchFilterUse the mail attribute of the user instead of
cnoruid. LDAP/Active Directory only
For example:In LDAP,
[user_store]
user_name_search_filter ="(&(objectClass=person)(mail=?))"
In Active Directory,[user_store]
user_name_search_filter ="(&(objectClass=user)(mail=?))"UserNameListFilterUse the mail attribute of the user if necessary. LDAP/Active Directory only
For example:In LDAP,
[user_store]
user_name_list_filter ="(&(objectClass=person)(!(sn=Service)))"
In Active Directory,[user_store]
user_name_list_filter ="(&(objectClass=user)(!(sn=Service)))"UsernameJavaScriptRegExChange this property that is under the relevant userstore manager tag as follows. This property allows you to add special characters like "@" in the username.
[user_store]
username_java_script_regex = '^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,4}$'UsernameJavaRegExThis is a regular expression to validate usernames. By default, strings have a length of 5 to 30. Only non-empty characters are allowed. You can provide ranges of alphabets, numbers and also ranges of ASCII values in the RegEx properties.
[user_store]
username_java_regex = '^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,4}'Realm configurations The username must use the email attribute of the admin user.
[super_admin]
username = "admin@wso2.com"
password = "admin"Note
Before this configuration, the user having the username admin and password admin was considered the super administrator. The super administrator user cannot be deleted.
After this configuration, the user having the username
admin@wso2.comis considered the super administrator. The user having the username admin is considered as a normal administrator.
Info
- With these configuration users can log in to super tenant with both
email username (
alex@gmail.com) or non-email usernames (larry). However, for tenants, only email usernames are allowed. (tod@gmail.com@wso2.com). - You can configure email username without enabling the
enable_email_domainproperty (step 5). Then users can log in to both the super tenant and the tenant using email and non-email usernames. However, super tenant users should always use @carbon.super at the end of usernames.
- With these configuration users can log in to super tenant with both
email username (
-
Restart the server.
Configure Salesforce as the Identity Provider¶
- Start the MWARE IAM if it is not started up already and log in using the email you configured in the realm as instructed in the above section.
- On the Management Console, navigate to Main > Identity > Identity Providers > Add.
-
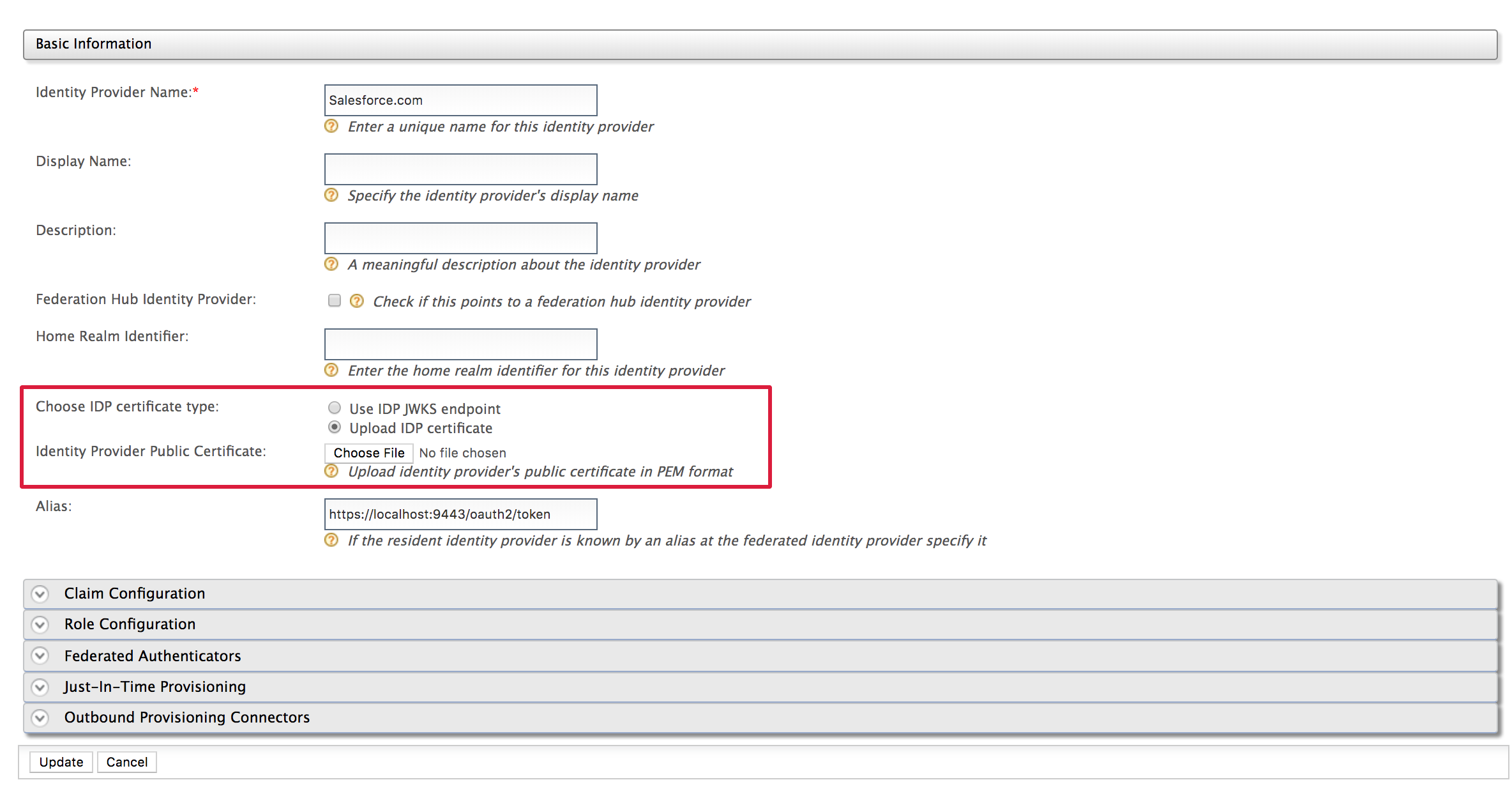
In the form that appears, provide a name for your identity provider by filling in the Identity Provider Name. You can use "Salesforce.com" as an example, but this can be any name you choose.
-
Upload the Salesforce public certificate that you generated and saved in step 5 under Configure Salesforce .
Do this by selecting Upload IDP certificate and clicking the Choose File button next to Identity Provider Public Certificate.Why is the certificate needed?
The Identity Provider's public certificate is used for SSL communication, to verify the signed data that comes from the Identity Provider and to send encrypted data to the Identity Provider.
-
Expand the Claim Configuration section of the form, followed by the Basic Claim Configuration section, and select Define Custom Claim Dialect.
Info
We are adding a claim map in order to provision the users claim values to salesforce when outbound provisioning users to salesforce via MWARE IAM. Here, the Identity Provider Claim URI is the claim URI in Salesforce, which maps local claim URI in WSO2 Identity Server. Read more about Claim Management.
-
Click Add Claim Mapping and add the following claims.
Local claims in MWARE IAM are unique URIs. These are mapped to the attributes required by salesforce to create a new profile . Therefore, in this step you are mapping the attributes required by Salesforce to a unique URI. Now, when creating a new profile/user MWARE IAM sends these values to the correct attribute of Salesforce.Identity Provider Claim URI Local Claim URI Alias http://wso2.org/claims/givennameEmail http://wso2.org/claims/emailaddressEmailEncodingKey http://wso2.org/claims/otherphoneLanguageLocaleKey http://wso2.org/claims/dobLastName http://wso2.org/claims/lastnameLocaleSidKey http://wso2.org/claims/primaryChallengeQuestionProfileId http://wso2.org/claims/roleTimeZoneSidKey http://wso2.org/claims/challengeQuestion1UserPermissionsCallCenterAutoLogin http://wso2.org/claims/telephoneUserPermissionsMarketingUser http://wso2.org/claims/mobileUserPermissionsOfflineUser http://wso2.org/claims/countryUsername http://wso2.org/claims/emailaddress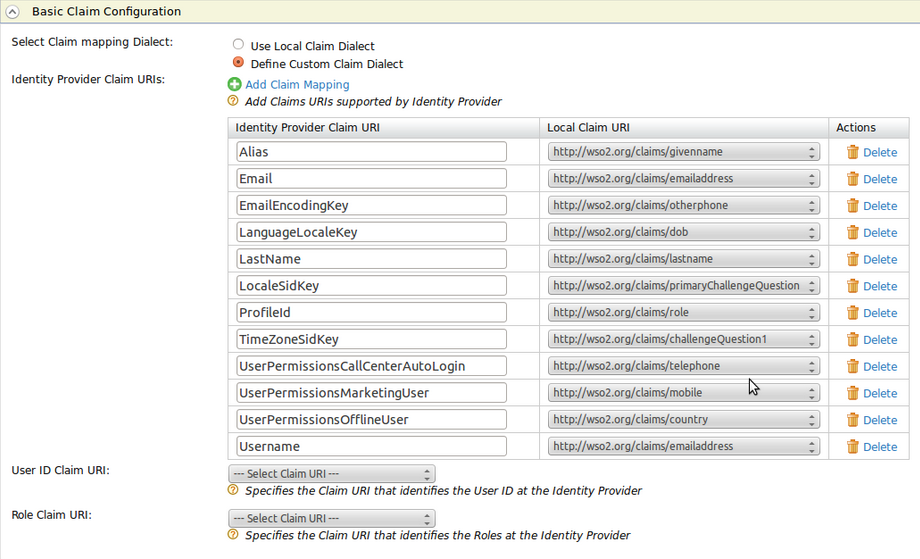
-
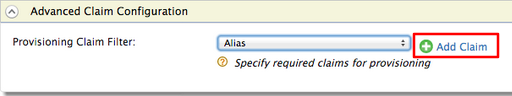
Expand the Advanced Claim Configuration section.
- Select the Claim URI you added from the Provisioning Claim
Filter dropdown and click Add Claim.
-
For each Claim URI, enter a default value as shown in the following table. The default values are used when creating the role in Salesforce.
For example, the alias, email, profile ID and all the values listed below are shown when a user is created.
These are sample values to help you understand better about claim URI and its value types.Claim URI Default Value Alias SamuelEmail samuel@wso2.comEmailEncodingKey UTF-8LanguageLocaleKey en_USLastName GnaniahLocaleSidKey en_USProfileId 00e90000001aV2oThe users that are added using MWARE IAM are added to this profile in Salesforce. For more information on the context of profiles in Salesforce, see the Salesforce tutorial.Tip
The ProfileId value refers to the ID of the profile you created in Salesforce step 4 of Configuring Salesforce. If it is the Chatter Free User profile you created, navigate to the profile in Salesforce to find the profile ID. You can do this by clicking Profiles under Manage Users in Salesforce and clicking Chatter Free User.
Copy the URL and decode it using a URL decoder. You get an output similar to what is shown below:
https://wso2-is-sso-dev-ed.lightning.force.com/one/one.app#/setup/page?nodeId=EnhancedProfiles&address=/ 00e90000001aV2o ?isdtp=p1&a:t=1509949702148In this case 00e90000001aV2o is your profile ID. Similarly, enter your Profile ID.
TimeZoneSidKey America/Los_AngelesUserPermissionsCallCenterAutoLogin falseUserPermissionsMarketingUser falseUserPermissionsOfflineUser falseUsername samuel@wso2.com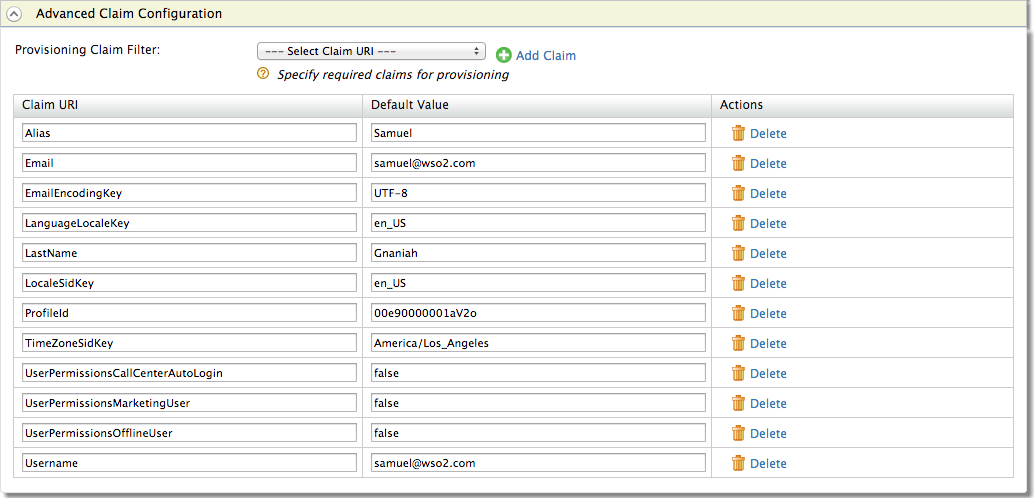
-
Expand the Outbound Provisioning Connectors section followed by the Salesforce Provisioning Configuration section.
-
Do the following configurations for Salesforce provisioning.
- Select Enable Connector to enable the Salesforce connector.
- Enter the API version. This is the version of the API you
are using in Salesforce.
Follow the steps given below to get the API version:- To obtain this, log into https://login.salesforce.com.
- Search for API in the Quick Find search box and click API.
- Generate any one of the WSDL's to check the version. You are navigated to page with XML syntaxes.
- On the top it will mention as "
Salesforce.com Enterprise Web Services API Version <VERSION>". For example:Salesforce.com Enterprise Web Services API Version 41.0 - Enter this value for the API version in the following
format:
v<VERSION_NUMBER>. For example:v41.0.
-
Enter the Domain. If you do not have a Salesforce domain, you need to create a domain by logging into https://login.salesforce.com.
Click here for more information on creating the domain on Salesforce.
- Search for My Domain in the search bar that is on the left
navigation panel.
- Click My Domain.
-
In the page that appears, come up with a name for your domain. You can check if the domain is available by clicking the Check Availability button. !!! info For the page given below to load on your browser, make sure that the Salesforce cookies are not blocked.
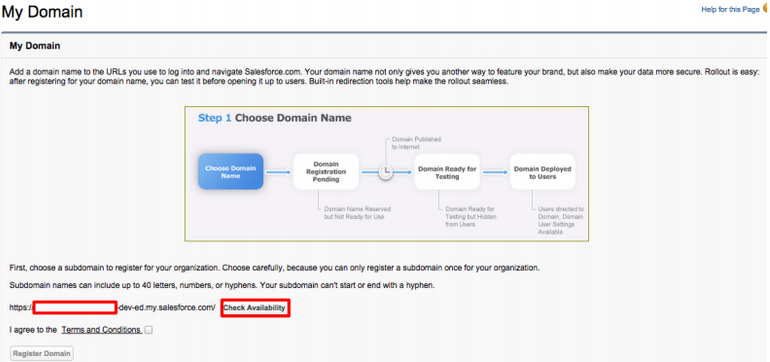
-
If the domain is available, select I agree to Terms and Conditions and click Register Domain to register your new domain.
-
Once the domain is registered to your account, click the Click here to login button to test this out.
Info
- Search for My Domain using the Quick Find search box and
click My Domain.
You see the domain as follows: Your domain name is<DOMAIN>-dev-ed.my.salesforce.com - Make sure you enter the domain with an HTTPS prefix so that
it resembles a URL:
https://<DOMAIN>-dev-ed.my.salesforce.com
.
- Search for My Domain in the search bar that is on the left
navigation panel.
-
Enter the Client ID. This is the Consumer Key obtained in step 3 when configuring Salesforce .
Did not save the details? Click here for more information on getting the details.
- Search for App Manager using the Quick Find search box and click App Manager.
- Click the expand button for your Connected App and click
View.
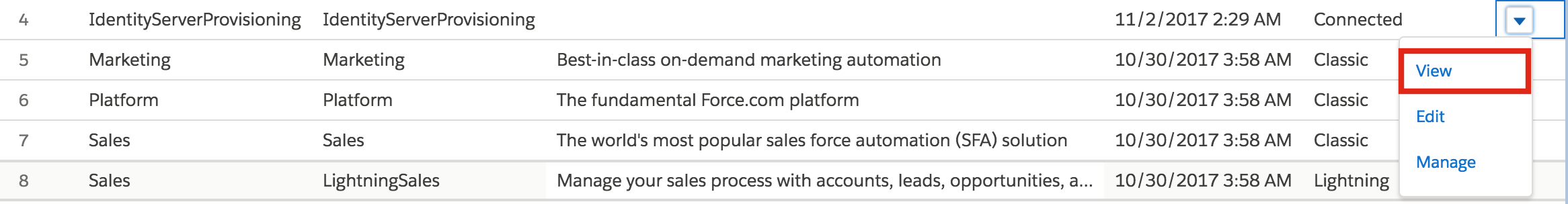
- You are navigated to the page that has the Client ID and Client Secret of the app under API (Enable OAuth Settings).
-
Enter the Client Secret. This is the Consumer Secret obtained in step 3 when configuring Salesforce .
- Enter the Username. This is the Salesforce username.
-
Enter the Password. This is the Salesforce password and must be entered along with the security token. So you would enter this in the following format:
<password><security_token>
For example, if your password istestpasswordand your security token is37f37f4433123, the value you would enter here istestpassword37f37f4433123.Where can I get the security token?
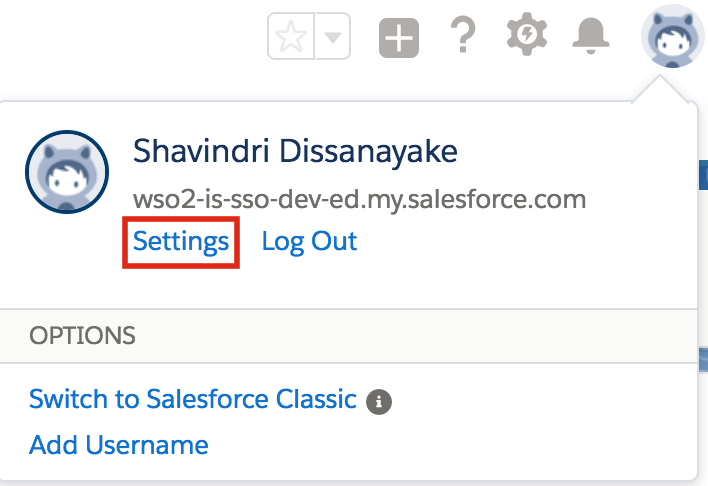
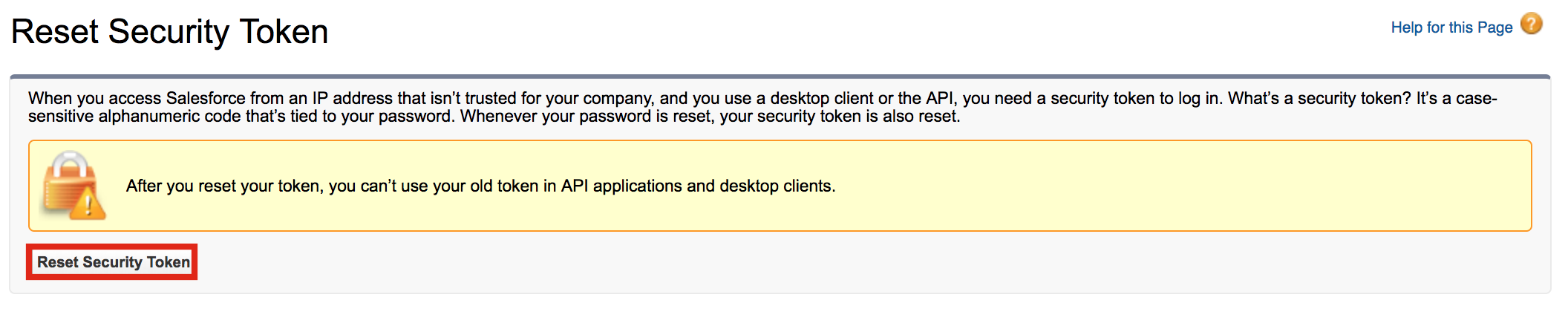
- Log in to Salesforce: https://login.salesforce.com/
- Click on your avatar and click My Settings. You are
navigated to the Personal Information page.
- On the left navigation, click Reset My Security Token
.
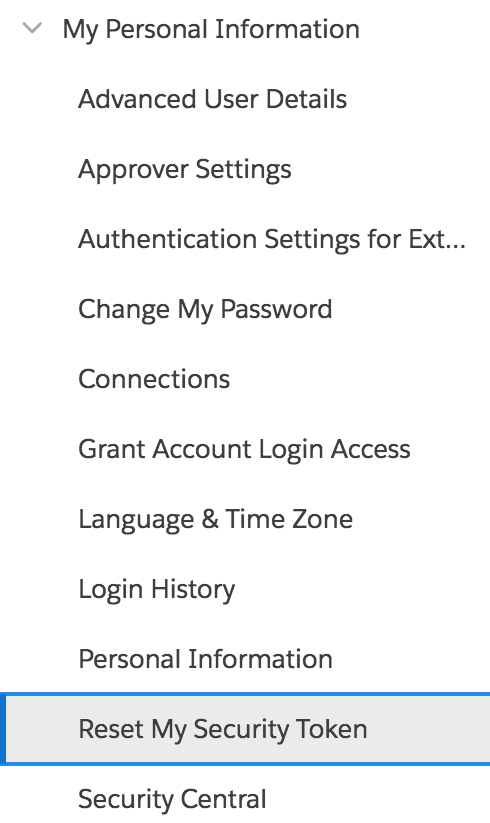 4. Click Reset Security Token.
4. Click Reset Security Token.
An email is sent to you with the new security token. Check the email of the email address you configured for Salesforce.
-
Click Register.
Configure MWARE IAM as the resident Service Provider¶
- In the Main menu under the Identity section, click Resident under Service Providers.
- Expand the Outbound Provisioning Configuration on the screen that appears.
-
Select the Google identity provider you configured from the drop down and click
+to add the IdP.Info
If you enable Blocking, Identity Server will wait for the response from the Identity Provider to continue.
If you enable Enable Rules and Blocking, blocking will block the provisioning till the rule completely evaluates and get the response back to the WSO2 IdP. Afterwards, you need to enable the XACML policy. For more information, see Rule-Based Provisioning
-
Click Update.
Add a user using SCIM.¶
You can also add users to Salesforce using SCIM.
Note
When adding the username, make sure to add an email address that is unique across all Salesforce organizations. The user might not be provisioned to Salesforce if the username already exists even in another Salesforce organization. For more information see the Salesforce documentation. Later on, if you want to update the user details, you won't be able to update the email address.
Select the correct SCIM user endpoint given in Resident > Inbound Provisioning Configuration and use it in the curl command.
The following is a sample cURL command to add users.
curl -v -k --header "Content-Type:application/json" --user kim@wso2.com:password --data '{"schemas": ["urn:scim:schemas:core:1.0"],"userName”:”kim@wso2.com","password”:”test123”,”name":{"familyName”:”paul”},”emails": [“kim@wso2.com"],"entitlements": [{"value":"00e2x000001AT3y","display":"ChatterFreeUser"}]}' https://localhost:9443/wso2/scim2/Users You can see that the user has been created in the "Users" section in salesforce.
Related topics